W&B Kubernetes Operator
Use the W&B Kubernetes Operator to simplify deploying, administering, troubleshooting, and scaling your W&B Server deployments on Kubernetes. You can think of the operator as a smart assistant for your W&B instance. The W&B Server architecture and design continuously evolves to expand AI developer tooling capabilities, and to provide appropriate primitives for high performance, better scalability, and easier administration. That evolution applies to the compute services, relevant storage and the connectivity between them. To help facilitate continuous updates and improvements across deployment types, W&B users a Kubernetes operator.W&B uses the operator to deploy and manage Dedicated Cloud instances on AWS, Google Cloud and Azure public clouds.
Reasons for the architecture shift
Historically, the W&B application was deployed as a single deployment and pod within a Kubernetes Cluster or a single Docker container. W&B has, and continues to recommend, to externalize the Database and Object Store. Externalizing the Database and Object store decouples the application’s state. As the application grew, the need to evolve from a monolithic container to a distributed system (microservices) was apparent. This change facilitates backend logic handling and seamlessly introduces built-in Kubernetes infrastructure capabilities. Distributed systems also supports deploying new services essential for additional features that W&B relies on. Before 2024, any Kubernetes-related change required manually updating the terraform-kubernetes-wandb Terraform module. Updating the Terraform module ensures compatibility across cloud providers, configuring necessary Terraform variables, and executing a Terraform apply for each backend or Kubernetes-level change. This process was not scalable since W&B Support had to assist each customer with upgrading their Terraform module. The solution was to implement an operator that connects to a central deploy.wandb.ai server to request the latest specification changes for a given release channel and apply them. Updates are received as long as the license is valid. Helm is used as both the deployment mechanism for the W&B operator and the means for the operator to handle all configuration templating of the W&B Kubernetes stack, Helm-ception.How it works
You can install the operator with helm or from the source. See charts/operator for detailed instructions. The installation process creates a deployment calledcontroller-manager and uses a custom resource definition named weightsandbiases.apps.wandb.com (shortName: wandb), that takes a single spec and applies it to the cluster:
controller-manager installs charts/operator-wandb based on the spec of the custom resource, release channel, and a user defined config. The configuration specification hierarchy enables maximum configuration flexibility at the user end and enables W&B to release new images, configurations, features, and Helm updates automatically.
Refer to the configuration specification hierarchy and configuration reference for configuration options.
The deployment consists of multiple pods, one per service. Each pod’s name is prefixed with wandb-.
Configuration specification hierarchy
Configuration specifications follow a hierarchical model where higher-level specifications override lower-level ones. Here’s how it works:- Release Channel Values: This base level configuration sets default values and configurations based on the release channel set by W&B for the deployment.
- User Input Values: Users can override the default settings provided by the Release Channel Spec through the System Console.
- Custom Resource Values: The highest level of specification, which comes from the user. Any values specified here override both the User Input and Release Channel specifications. For a detailed description of the configuration options, see Configuration Reference.
Before you begin
- Refer to the reference architecture for complete infrastructure requirements, including:
- Software version requirements (Kubernetes, MySQL, Redis, Helm)
- Hardware requirements (CPU architecture, sizing recommendations)
- Networking, SSL/TLS, and DNS requirements
- Obtain a valid W&B Server license.
- See the following sections and the bare-metal installation guide for detailed instructions to set up and configure W&B Self-Managed. Depending on the installation method, you might need to install additional software or meet additional requirements.
MySQL Database
W&B requires an external MySQL database. For production, W&B strongly recommends using managed database services: Managed database services provide automated backups, monitoring, high availability, patching, and reduce operational overhead. See the reference architecture for complete MySQL requirements, including sizing recommendations and configuration parameters. For database creation SQL, see the bare-metal guide. For questions about your deployment’s database configuration, contact support or your AISE.Redis
W&B depends on a single-node Redis 7.x deployment used by W&B’s components for job queuing and data caching. For convenience during testing and development of proofs of concept, W&B Self-Managed includes a local Redis deployment that is not appropriate for production deployments. For production deployments, W&B can connect to a Redis instance in the following environments:- AWS Elasticache
- Google Cloud Memory Store
- Azure Cache for Redis
- Redis deployment hosted in your cloud or on-premise infrastructure
Object storage
W&B requires object storage with pre-signed URL and CORS support. For production deployments, W&B recommends using managed object storage services:- Amazon S3: Object storage service offering industry-leading scalability, data availability, security, and performance.
- Google Cloud Storage: Managed service for storing unstructured data at scale.
- Azure Blob Storage: Cloud-based object storage solution for storing massive amounts of unstructured data.
- CoreWeave AI Object Storage: High-performance, S3-compatible object storage service optimized for AI workloads.
MinIO Open Source is in maintenance mode with no active development or pre-compiled binaries. For production deployments, W&B recommends using managed object storage services or enterprise-grade S3-compatible solutions.
Networking requirements
For a networked deployment, egress to these endpoints is required during both installation and runtime:- https://deploy.wandb.ai
- https://charts.wandb.ai
- https://quay.io (used for Prometheus images)
Additional container registries may be required depending on your deployment configuration:
https://gcr.iois needed when deploying Bufstream and etcd for Weave online evaluations.
SSL/TLS requirements
W&B requires a valid signed SSL/TLS certificate for secure communication between clients and the server. SSL/TLS termination must occur on the ingress/load balancer. The W&B Server application does not terminate SSL or TLS connections. Important: W&B does not support self-signed certificates and custom CAs. Using self-signed certificates will cause challenges for users and is not supported. If possible, using a service like Let’s Encrypt is a great way to provide trusted certificates to your load balancer. Services like Caddy and Cloudflare manage SSL for you. If your security policies require SSL communication within your trusted networks, consider using a tool like Istio and side car containers.Air-gapped installations
See the Deploy W&B in airgapped environment with Kubernetes tutorial on how to install the W&B Kubernetes Operator in an airgapped environment.OpenShift Kubernetes clusters
W&B supports deployment on OpenShift Kubernetes clusters in cloud, on-premises, and air-gapped environments.W&B recommends you install with the official W&B Helm chart.
Run the container as an un-privileged user
By default, containers use a$UID of 999. Specify $UID >= 100000 and a $GID of 0 if your orchestrator requires the container run with a non-root user.
W&B must start as the root group (
$GID=0) for file system permissions to function properly.app or console. For details, see Custom security context.
Deploy W&B Server application
The W&B Kubernetes Operator with Helm is the recommended installation method for all W&B Self-Managed deployments, including cloud, on-premises, and air-gapped environments.
- Helm CLI: Direct deployment using Helm commands
- Helm Terraform Module: Infrastructure-as-code deployment
- W&B Cloud Terraform Modules: Complete infrastructure + application deployment for AWS, Google Cloud, and Azure
- Deploy W&B Platform On-premises for datacenter/bare-metal environments
- Kubernetes operator for air-gapped instances for disconnected environments
Deploy W&B with Helm CLI
W&B provides a Helm Chart to deploy the W&B Kubernetes operator to a Kubernetes cluster. This approach allows you to deploy W&B Server with Helm CLI or a continuous delivery tool like ArgoCD. Make sure that the above mentioned requirements are in place. Follow those steps to install the W&B Kubernetes Operator with Helm CLI:-
Add the W&B Helm repository. The W&B Helm chart is available in the W&B Helm repository:
-
Install the Operator on a Kubernetes cluster:
-
Configure the W&B operator custom resource to trigger the W&B Server installation. Create a file named
operator.yamlwith your W&B deployment configuration. Refer to Configuration Reference for all available options. Here’s a minimal example configuration: -
Start the Operator with your custom configuration so that it can install, configure, and manage the W&B Server application:
Wait until the deployment completes. This takes a few minutes.
- To verify the installation using the web UI, create the first admin user account, then follow the verification steps outlined in Verify the installation.
Deploy W&B with Helm Terraform Module
This method allows for customized deployments tailored to specific requirements, leveraging Terraform’s infrastructure-as-code approach for consistency and repeatability. The official W&B Helm-based Terraform Module is located here. The following code can be used as a starting point and includes all necessary configuration options for a production grade deployment.Deploy W&B with W&B Cloud Terraform modules
W&B provides a set of Terraform Modules for AWS, Google Cloud and Azure. Those modules deploy entire infrastructures including Kubernetes clusters, load balancers, MySQL databases and so on as well as the W&B Server application. The W&B Kubernetes Operator is already pre-baked with those official W&B cloud-specific Terraform Modules with the following versions:| Terraform Registry | Source Code | Version |
|---|---|---|
| AWS | https://github.com/wandb/terraform-aws-wandb | v4.0.0+ |
| Azure | https://github.com/wandb/terraform-azurerm-wandb | v2.0.0+ |
| Google Cloud | https://github.com/wandb/terraform-google-wandb | v2.0.0+ |
Verify the installation
To verify the installation, W&B recommends using the W&B CLI. The verify command executes several tests that verify all components and configurations.This step assumes that the first admin user account is created with the browser.
- Install the W&B CLI:
- Log in to W&B:
- Verify the installation:
Access the W&B Management Console
The W&B Kubernetes operator comes with a management console. It is located at${HOST_URI}/console, for example https://wandb.company-name.com/console.
There are two ways to log in to the management console:
- Option 1 (Recommended)
- Option 2
-
Open the W&B application in the browser and login. Log in to the W&B application with
${HOST_URI}/, for examplehttps://wandb.company-name.com/ -
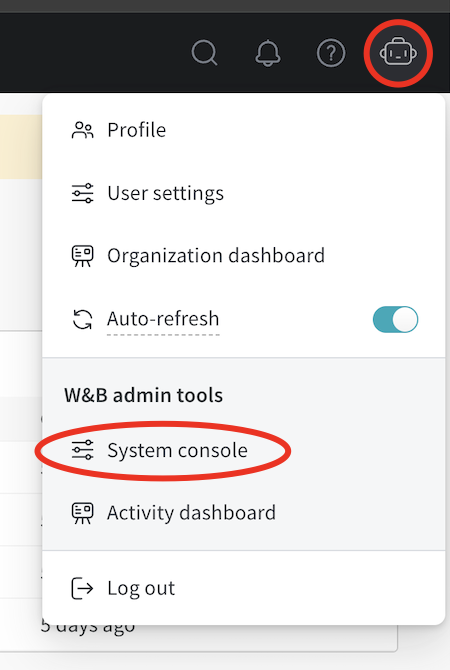
Access the console. Click on the icon in the top right corner and then click System console. Only users with admin privileges can see the System console entry.
Update the W&B Kubernetes operator
This section describes how to update the W&B Kubernetes operator.- Updating the W&B Kubernetes operator does not update the W&B server application.
- See the instructions here if you use a Helm chart that does not user the W&B Kubernetes operator before you follow the proceeding instructions to update the W&B operator.
-
First, update the repo with
helm repo update: -
Next, update the Helm chart with
helm upgrade:
Update the W&B Server application
You no longer need to update W&B Server application if you use the W&B Kubernetes operator. The operator automatically updates your W&B Server application when a new version of the software of W&B is released.Migrate Self-Managed instances to W&B Operator
The proceeding section describe how to migrate from self-managing your own W&B Server installation to using the W&B Operator to do this for you. The migration process depends on how you installed W&B Server:The W&B Operator is the default and recommended installation method for W&B Server. Reach out to Customer Support or your W&B team if you have any questions.
- If you used the official W&B Cloud Terraform Modules, navigate to the appropriate documentation and follow the steps there:
- If you used the W&B Non-Operator Helm chart, continue here.
- If you used the W&B Non-Operator Helm chart with Terraform, continue here.
- If you created the Kubernetes resources with manifests, continue here.
Migrate to Operator-based AWS Terraform Modules
For a detailed description of the migration process, continue here.Migrate to Operator-based Google Cloud Terraform Modules
Reach out to Customer Support or your W&B team if you have any questions or need assistance.Migrate to Operator-based Azure Terraform Modules
Reach out to Customer Support or your W&B team if you have any questions or need assistance.Migrate to Operator-based Helm chart
Follow these steps to migrate to the Operator-based Helm chart:-
Get the current W&B configuration. If W&B was deployed with an non-operator-based version of the Helm chart, export the values like this:
If W&B was deployed with Kubernetes manifests, export the values like this:You now have all the configuration values you need for the next step.
-
Create a file called
operator.yaml. Follow the format described in the Configuration Reference. Use the values from step 1. -
Scale the current deployment to 0 pods. This step is stops the current deployment.
-
Update the Helm chart repo:
-
Install the new Helm chart:
-
Configure the new helm chart and trigger W&B application deployment. Apply the new configuration.
The deployment takes a few minutes to complete.
- Verify the installation. Make sure that everything works by following the steps in Verify the installation.
- Remove to old installation. Uninstall the old helm chart or delete the resources that were created with manifests.
Migrate to Operator-based Terraform Helm chart
Follow these steps to migrate to the Operator-based Helm chart:- Prepare Terraform config. Replace the Terraform code from the old deployment in your Terraform config with the one that is described here. Set the same variables as before. Do not change .tfvars file if you have one.
- Execute Terraform run. Execute terraform init, plan and apply
- Verify the installation. Make sure that everything works by following the steps in Verify the installation.
- Remove to old installation. Uninstall the old helm chart or delete the resources that were created with manifests.
Configuration Reference for W&B Server
This section describes the configuration options for W&B Server application. The application receives its configuration as custom resource definition named WeightsAndBiases. Some configuration options are exposed with the below configuration, some need to be set as environment variables. The documentation has two lists of environment variables: basic and advanced. Only use environment variables if the configuration option that you need is not exposed using the Helm Chart.Basic example
This example defines the minimum set of values required for W&B. For a more realistic production example, see Complete example. This YAML file defines the desired state of your W&B deployment, including the version, environment variables, external resources like databases, and other necessary settings.Complete example
This example configuration deploys W&B to Google Cloud Anthos using Google Cloud Storage:Host
Object storage (bucket)
AWSkmsKey must be null.
To reference accessKey and secretKey from a secret:
MySQL
password from a secret:
License
license from a secret:
Ingress
To identify the ingress class, see this FAQ entry. Without TLSCustom Kubernetes ServiceAccounts
Specify custom Kubernetes service accounts to run the W&B pods. The following snippet creates a service account as part of the deployment with the specified name:create: false:
External Redis
password from a secret:
LDAP
Configure LDAP by setting environment variables inglobal.extraEnv:
OIDC SSO
authMethod is optional.
SMTP
Environment Variables
Custom certificate authority
customCACerts is a list and can take many certificates. Certificate authorities specified in customCACerts only apply to the W&B Server application.
If using a ConfigMap, each key in the ConfigMap must end with
.crt (for example, my-cert.crt or ca-cert1.crt). This naming convention is required for update-ca-certificates to parse and add each certificate to the system CA store.Custom security context
Each W&B component supports custom security context configurations of the following form:The only valid value for
runAsGroup: is 0. Any other value is an error.app to your configuration:
console, weave, weave-trace and parquet.
Configuration Reference for W&B Operator
This section describes configuration options for W&B Kubernetes operator (wandb-controller-manager). The operator receives its configuration in the form of a YAML file.
By default, the W&B Kubernetes operator does not need a configuration file. Create a configuration file if required. For example, you might need a configuration file to specify custom certificate authorities, deploy in an air gap environment and so forth.
Find the full list of spec customization in the Helm repository.
Custom CA
A custom certificate authority (customCACerts), is a list and can take many certificates. Those certificate authorities when added only apply to the W&B Kubernetes operator (wandb-controller-manager).
Each key in the ConfigMap must end with
.crt (e.g., my-cert.crt or ca-cert1.crt). This naming convention is required for update-ca-certificates to parse and add each certificate to the system CA store.FAQ
What is the purpose/role of each individual pod?
wandb-app: the core of W&B, including the GraphQL API and frontend application. It powers most of our platform’s functionality.wandb-console: the administration console, accessed via/console.wandb-otel: the OpenTelemetry agent, which collects metrics and logs from resources at the Kubernetes layer for display in the administration console.wandb-prometheus: the Prometheus server, which captures metrics from various components for display in the administration console.wandb-parquet: a backend microservice separate from thewandb-apppod that exports database data to object storage in Parquet format.wandb-weave: another backend microservice that loads query tables in the UI and supports various core app features.wandb-weave-trace: a framework for tracking, experimenting with, evaluating, deploying, and improving LLM-based applications. The framework is accessed via thewandb-apppod.
How to get the W&B Operator Console password
See Accessing the W&B Kubernetes Operator Management Console.How to access the W&B Operator Console if Ingress doesn’t work
Execute the following command on a host that can reach the Kubernetes cluster:https://localhost:8082/ console.
See Accessing the W&B Kubernetes Operator Management Console on how to get the password (Option 2).