OpenID Connect (OIDC)
W&B supports the following OIDC authentication flows for integrating with external Identity Providers (IdPs).- Implicit Flow with Form Post
- Authorization Code Flow with Proof Key for Code Exchange (PKCE)
Configure your IdP
This section shows how to configure your identity provider (IdP) for OIDC. Select the tab for your IdP for details.- Cognito
- Okta
- Entra
Follow the procedure below to set up AWS Cognito for authorization:
-
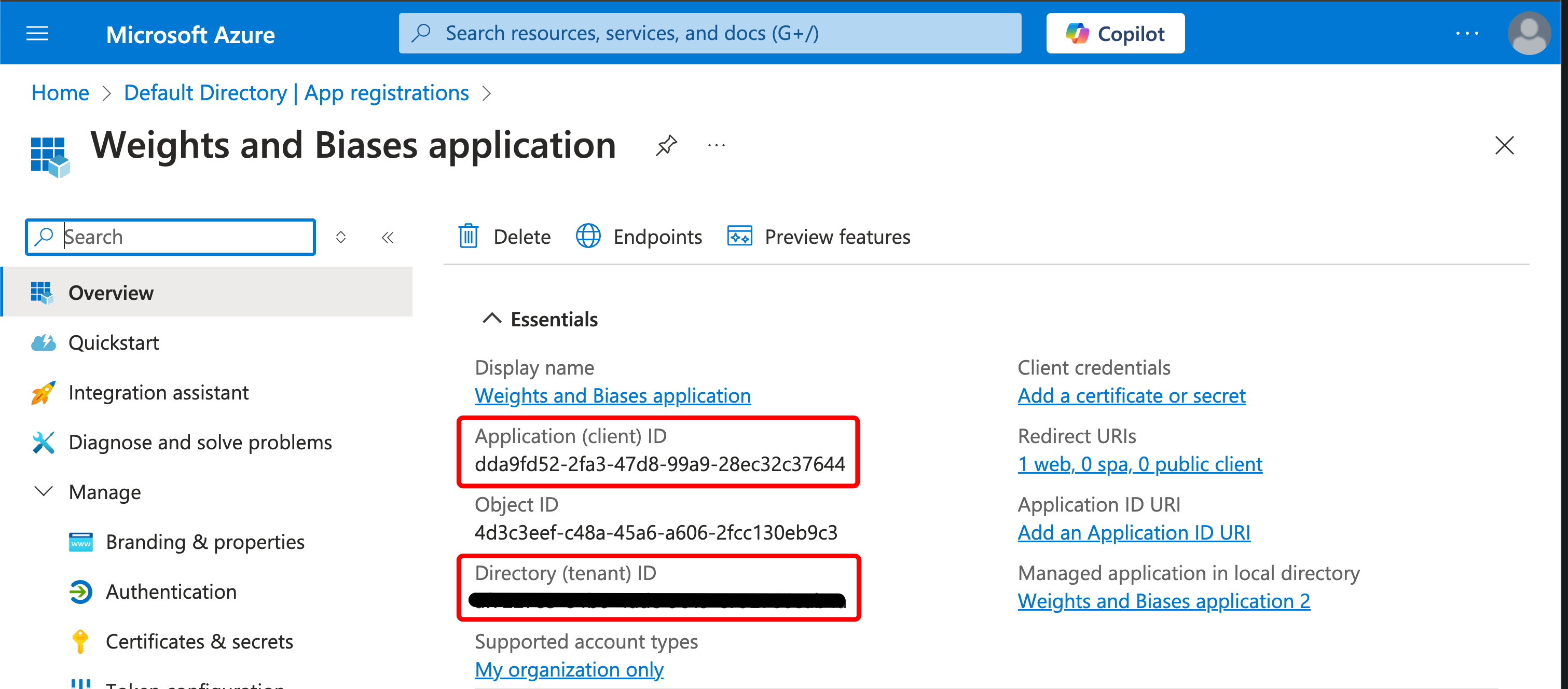
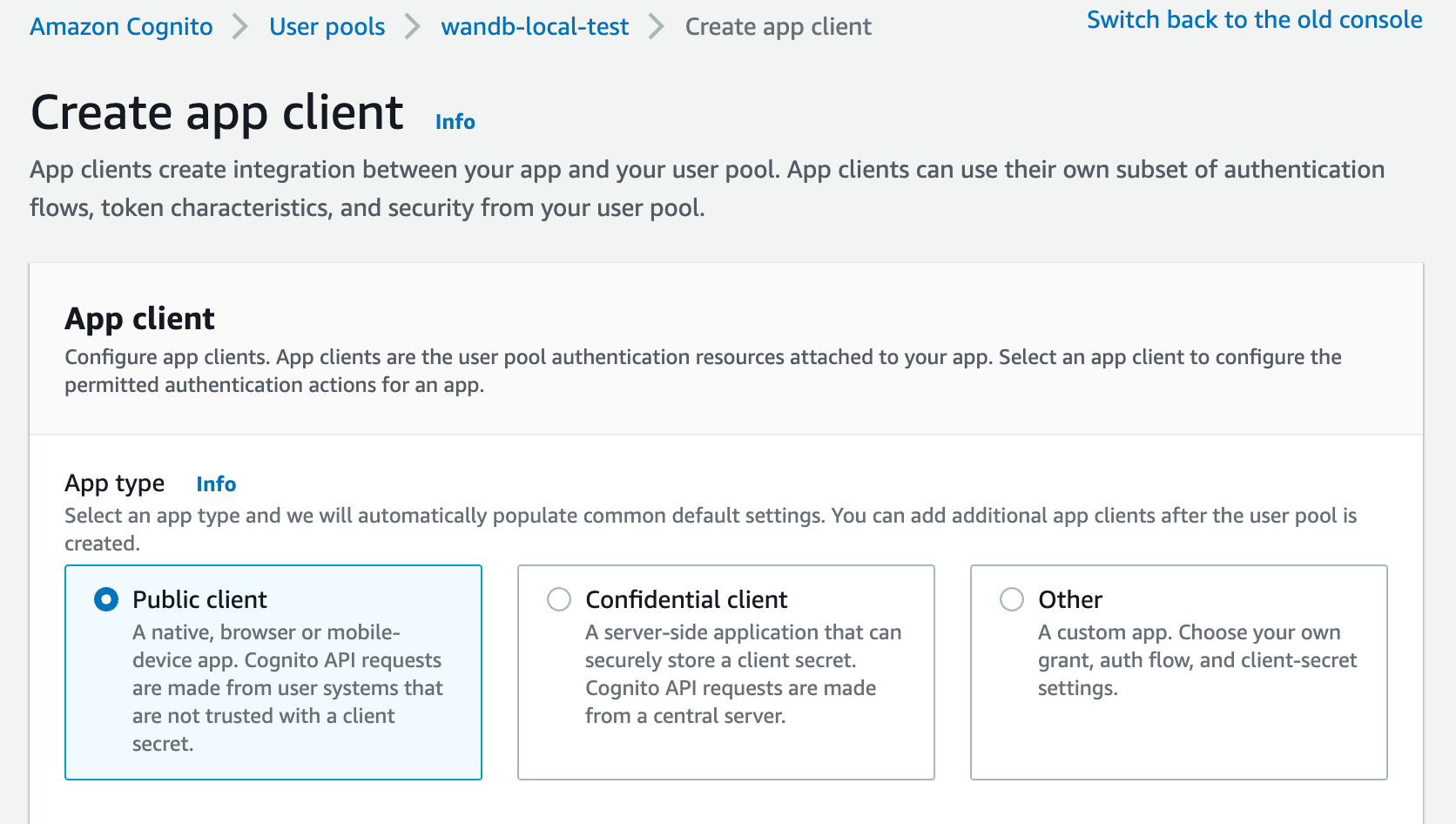
First, sign in to your AWS account and navigate to the AWS Cognito App.
-
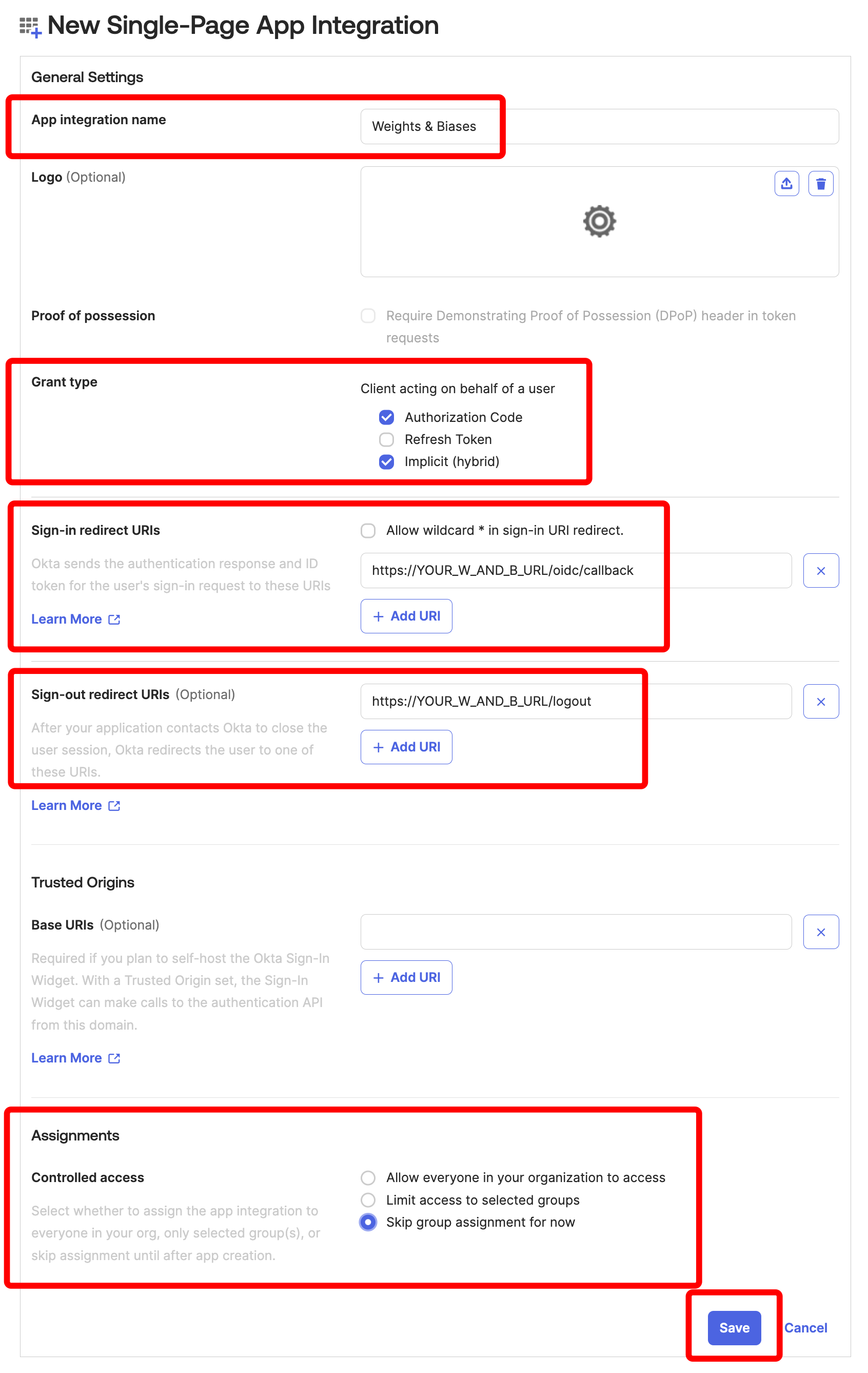
Provide an allowed callback URL to configure the application in your IdP:
- Add
http(s)://YOUR-W&B-HOST/oidc/callbackas the callback URL. ReplaceYOUR-W&B-HOSTwith your W&B host path.
- Add
-
If your IdP supports universal logout, set the Logout URL to
http(s)://YOUR-W&B-HOST. ReplaceYOUR-W&B-HOSTwith your W&B host path. For example, if your application was running athttps://wandb.mycompany.com, you would replaceYOUR-W&B-HOSTwithwandb.mycompany.com. The image below demonstrates how to provide allowed callback and sign-out URLs in AWS Cognito.wandb/local uses the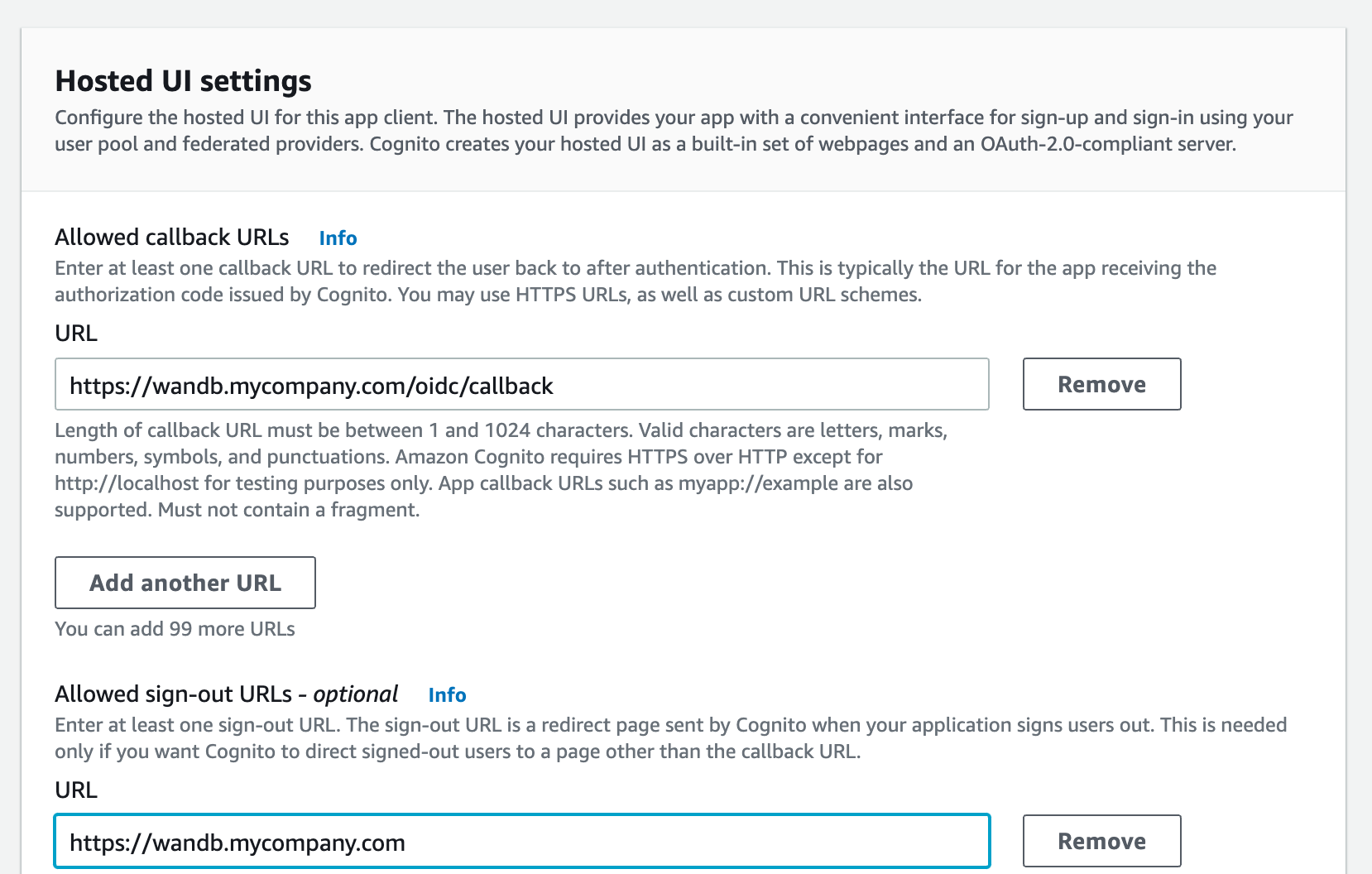
implicitgrant with theform_postresponse type by default. You can also configure wandb/local to perform anauthorization_codegrant that uses the PKCE Code Exchange flow. - Select one or more OAuth grant types to configure how AWS Cognito delivers tokens to your app.
-
W&B requires specific OpenID Connect (OIDC) scopes. Select the following from AWS Cognito App:
- “openid”
- “profile”
- “email”
Select the Auth Method in the settings page or set the OIDC_AUTH_METHOD environment variable to tell wandb/local which grant to. You must set the Auth Method to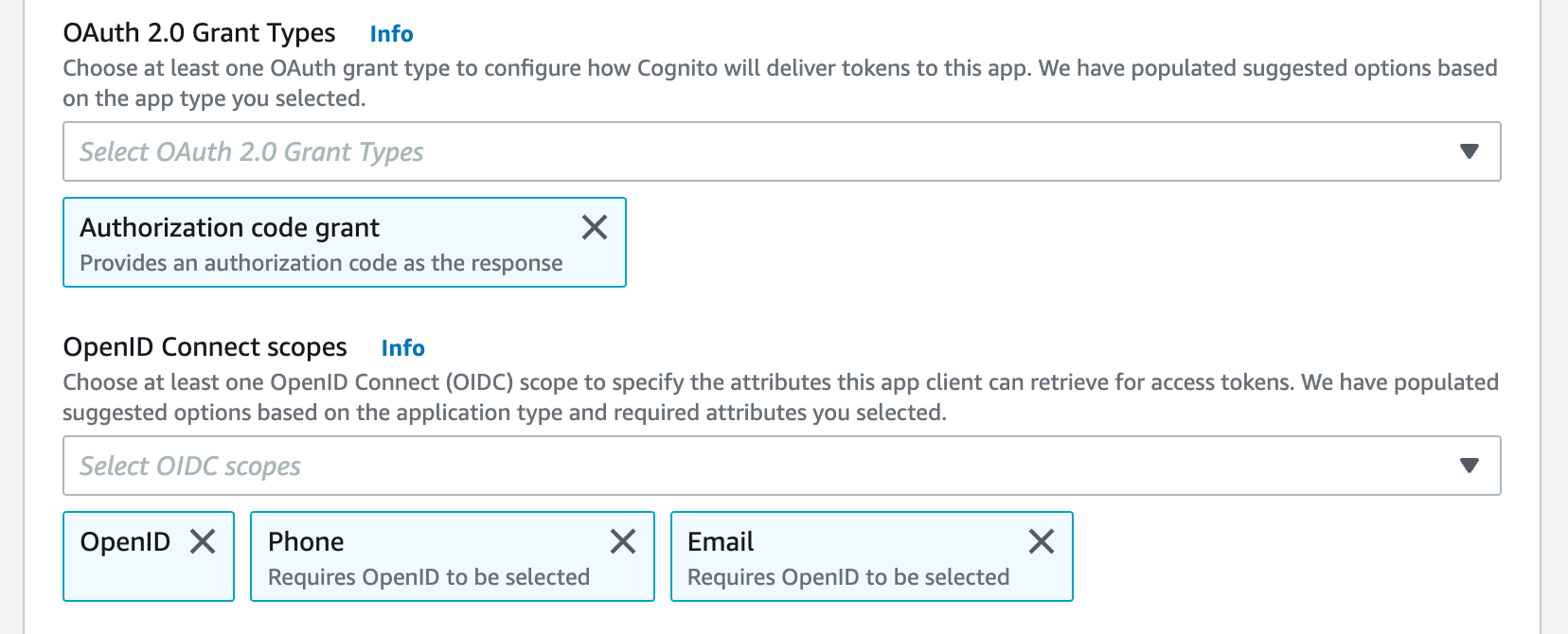
pkce. -
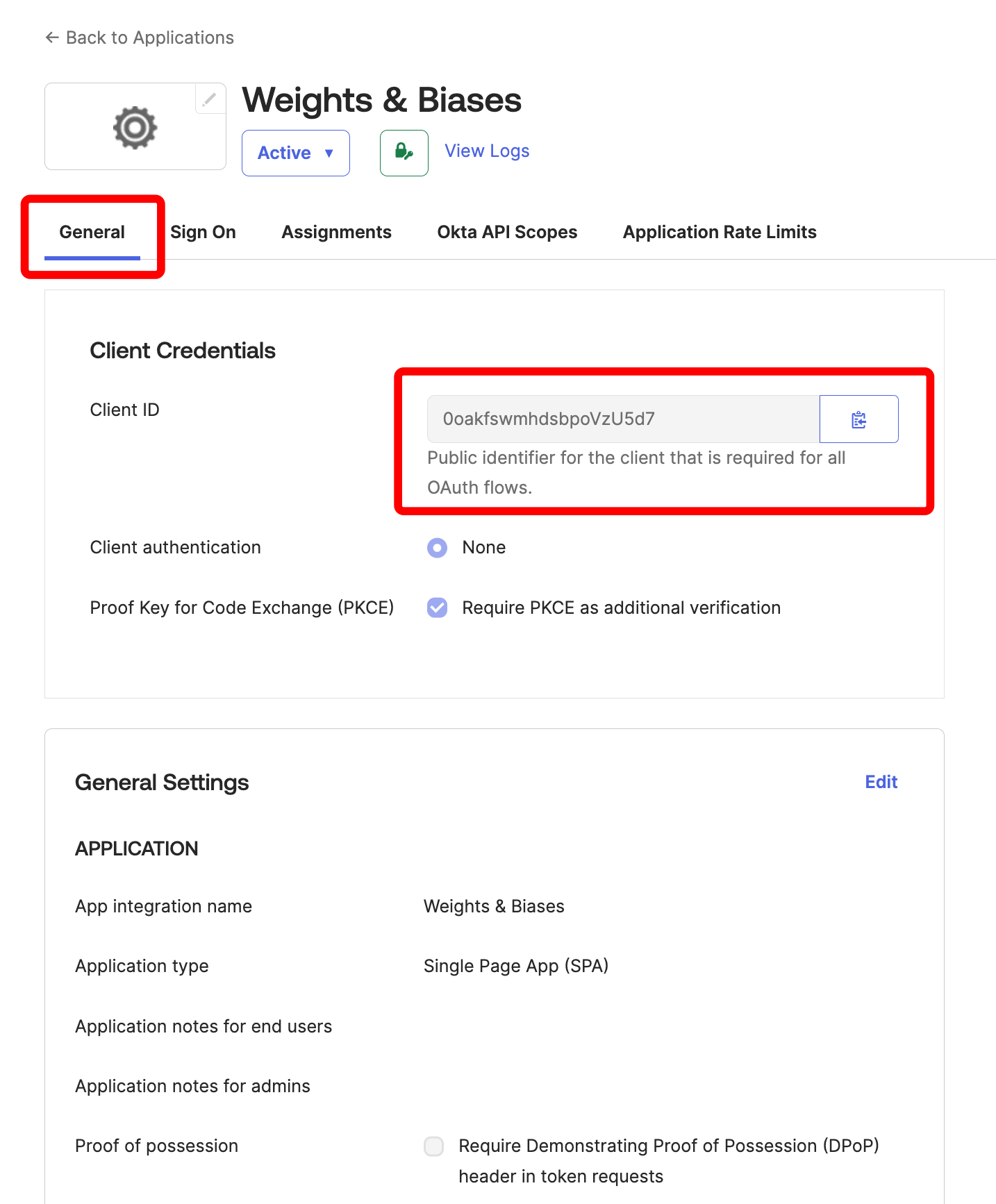
You need a Client ID and the URL of your OIDC issuer. The OpenID discovery document must be available at
$OIDC_ISSUER/.well-known/openid-configurationFor example, , you can generate your issuer URL by appending your User Pool ID to the Cognito IdP URL from the App Integration tab within the User Pools section:Do not use the “Cognito domain” for the IDP URL. Cognito provides it’s discovery document at
https://cognito-idp.$REGION.amazonaws.com/$USER_POOL_ID
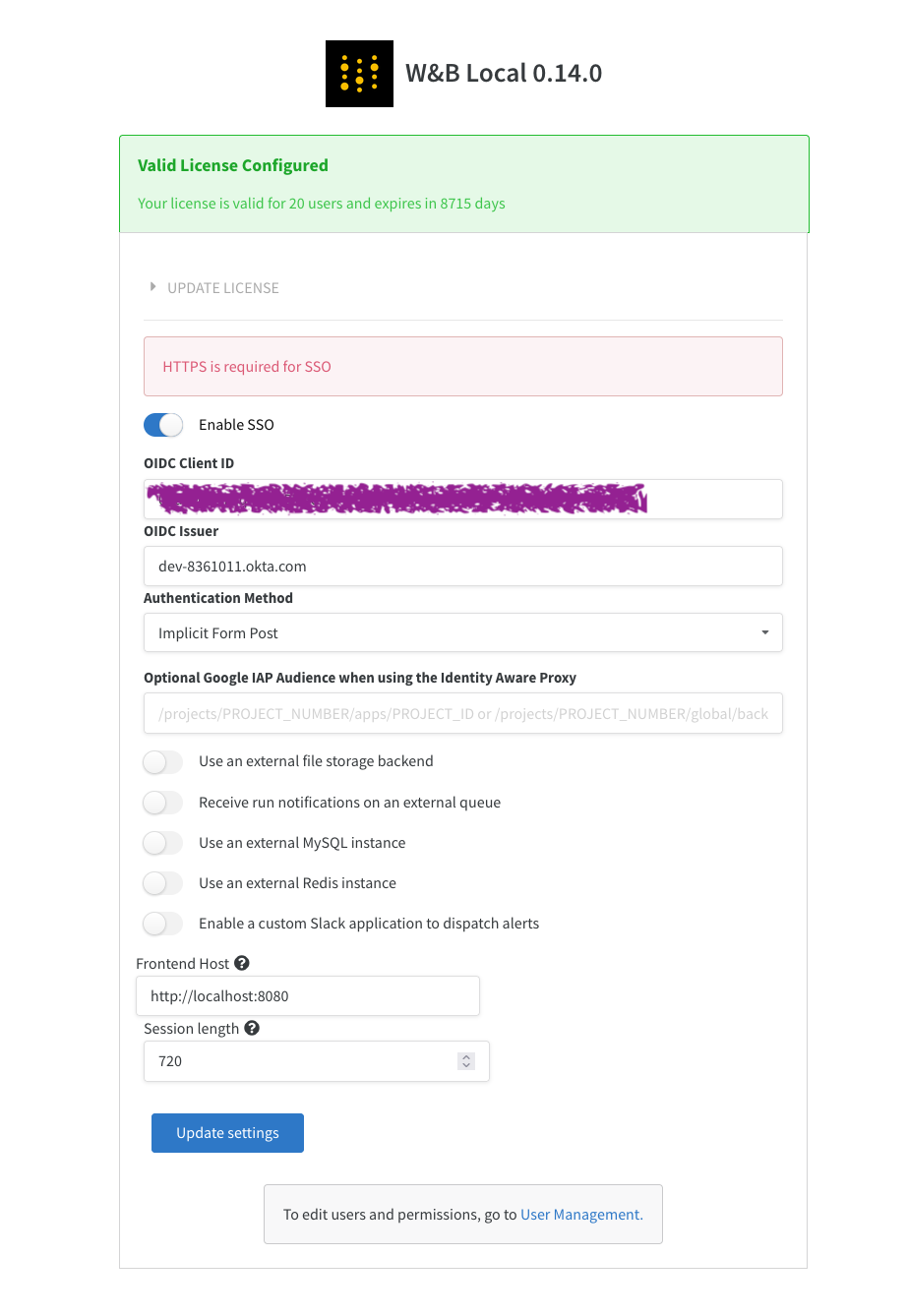
Set up SSO in W&B
To set up SSO, you need administrator privileges and the following information:- OIDC Client ID
- OIDC Auth method (
implicitorpkce) - OIDC Issuer URL
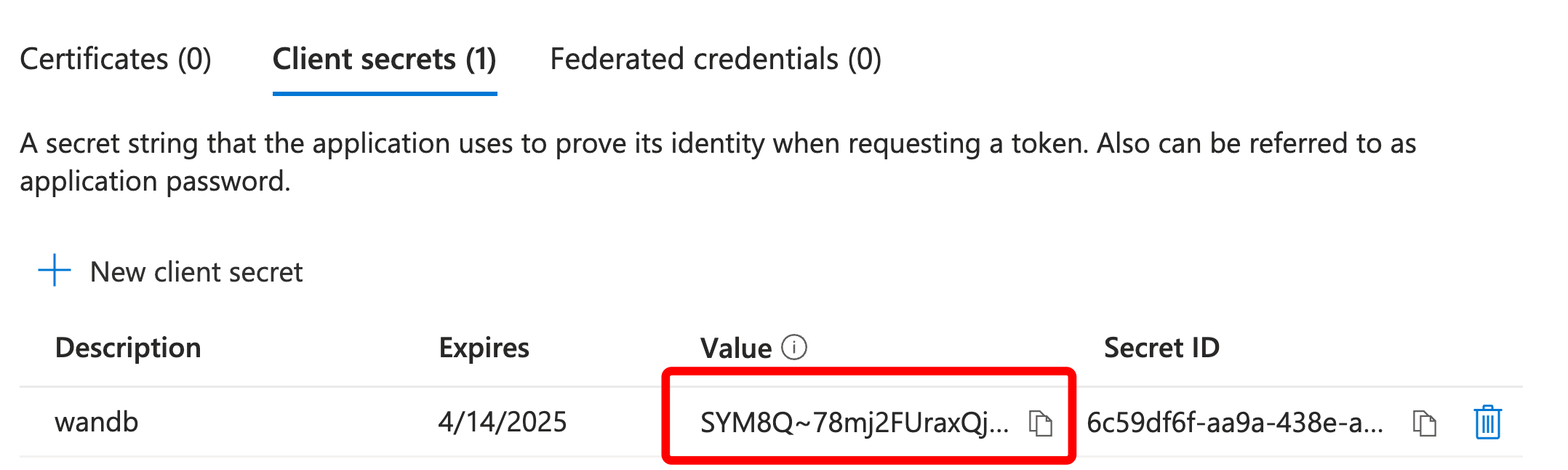
- OIDC Client Secret (optional; depends on how you have setup your IdP)
GORILLA_OIDC_SECRET.
- In the W&B App, go to System Console > Settings > Advanced > User Spec and add
GORILLA_OIDC_SECRETto theextraENVsection as shown below. - In Helm, configure
values.global.extraEnvas shown below.
If you’re unable to log in to your instance after configuring SSO, you can restart the instance with the
LOCAL_RESTORE=true environment variable set. This outputs a temporary password to the containers logs and disables SSO. Once you’ve resolved any issues with SSO, you must remove that environment variable to enable SSO again.- System Console
- System settings
The System Console is the successor to the System Settings page. It is available with the W&B Kubernetes Operator based deployment.
- Refer to Access the W&B Management Console.
-
Navigate to Settings, then Authentication. Select OIDC in the Type dropdown.
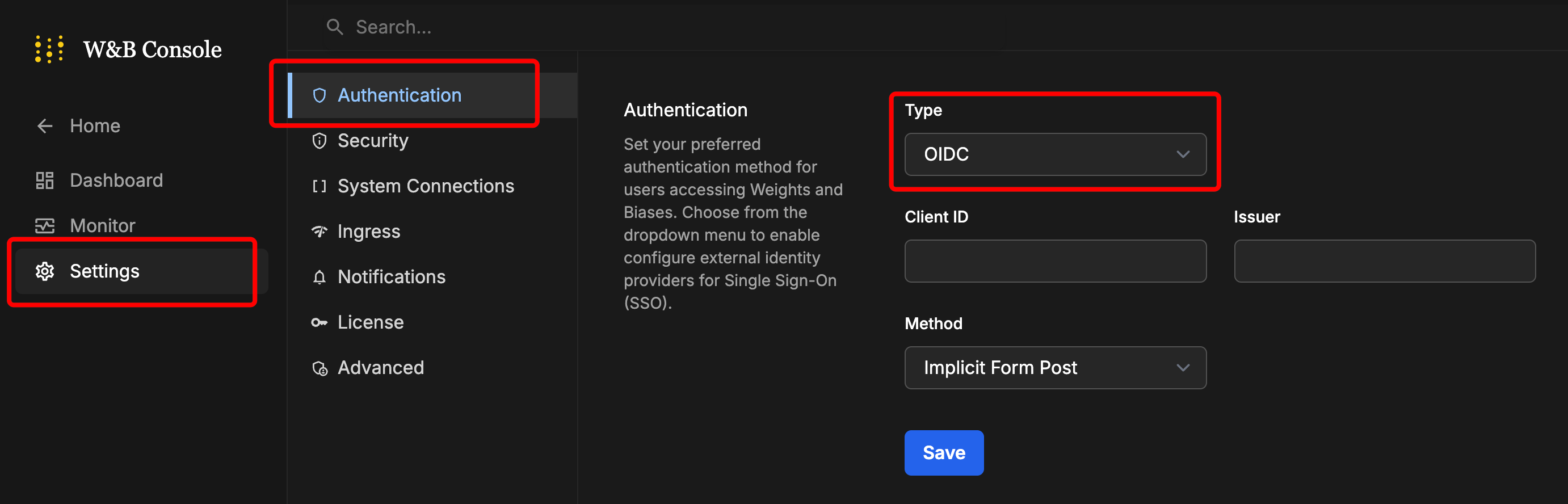
- Enter the values.
- Click on Save.
- Log out and then log back in, this time using the IdP login screen.
Find your customer namespace
Before you can configure team-level BYOB with CoreWeave storage on W&B Dedicated Cloud or Self-Managed, you need to obtain your organization’s Customer Namespace. You can view and copy it from the bottom of the Authentication tab.For detailed instructions on configuring CoreWeave storage with your Customer Namespace, see CoreWeave requirements for Dedicated Cloud / Self-Managed.If you’re unable to log in to your instance after configuring SSO, you can restart the instance with the
LOCAL_RESTORE=true environment variable set. This outputs a temporary password to the containers logs and turn off SSO. Once you’ve resolved any issues with SSO, you must remove that environment variable to enable SSO again.