Configure SSO with OIDC
6 minute read
W&B Server’s support for OpenID Connect (OIDC) compatible identity providers allows for management of user identities and group memberships through external identity providers like Okta, Keycloak, Auth0, Google, and Entra.
OpenID Connect (OIDC)
W&B Server supports the following OIDC authentication flows for integrating with external Identity Providers (IdPs).
- Implicit Flow with Form Post
- Authorization Code Flow with Proof Key for Code Exchange (PKCE)
These flows authenticate users and provide W&B Server with the necessary identity information (in the form of ID tokens) to manage access control.
The ID token is a JWT that contains the user’s identity information, such as their name, username, email, and group memberships. W&B Server uses this token to authenticate the user and map them to appropriate roles or groups in the system.
In the context of W&B Server, access tokens authorize requests to APIs on behalf of the user, but since W&B Server’s primary concern is user authentication and identity, it only requires the ID token.
You can use environment variables to configure IAM options for your Dedicated cloud or Self-managed instance.
To assist with configuring Identity Providers for Dedicated cloud or Self-managed W&B Server installations, follow these guidelines to follow for various IdPs. If you’re using the SaaS version of W&B, reach out to support@wandb.com for assistance in configuring an Auth0 tenant for your organization.
Follow the procedure below to set up AWS Cognito for authorization:
-
First, sign in to your AWS account and navigate to the AWS Cognito App.
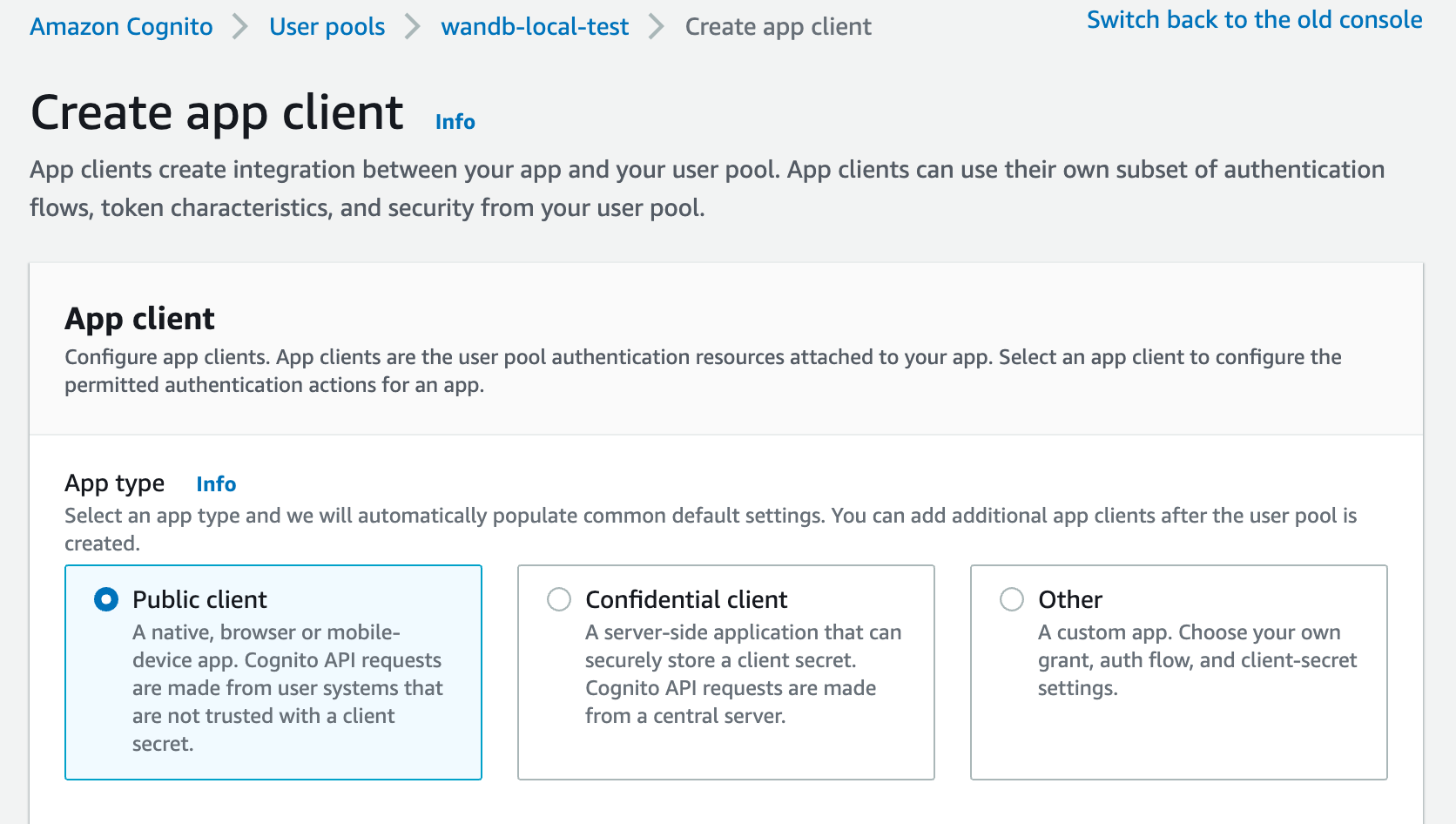
-
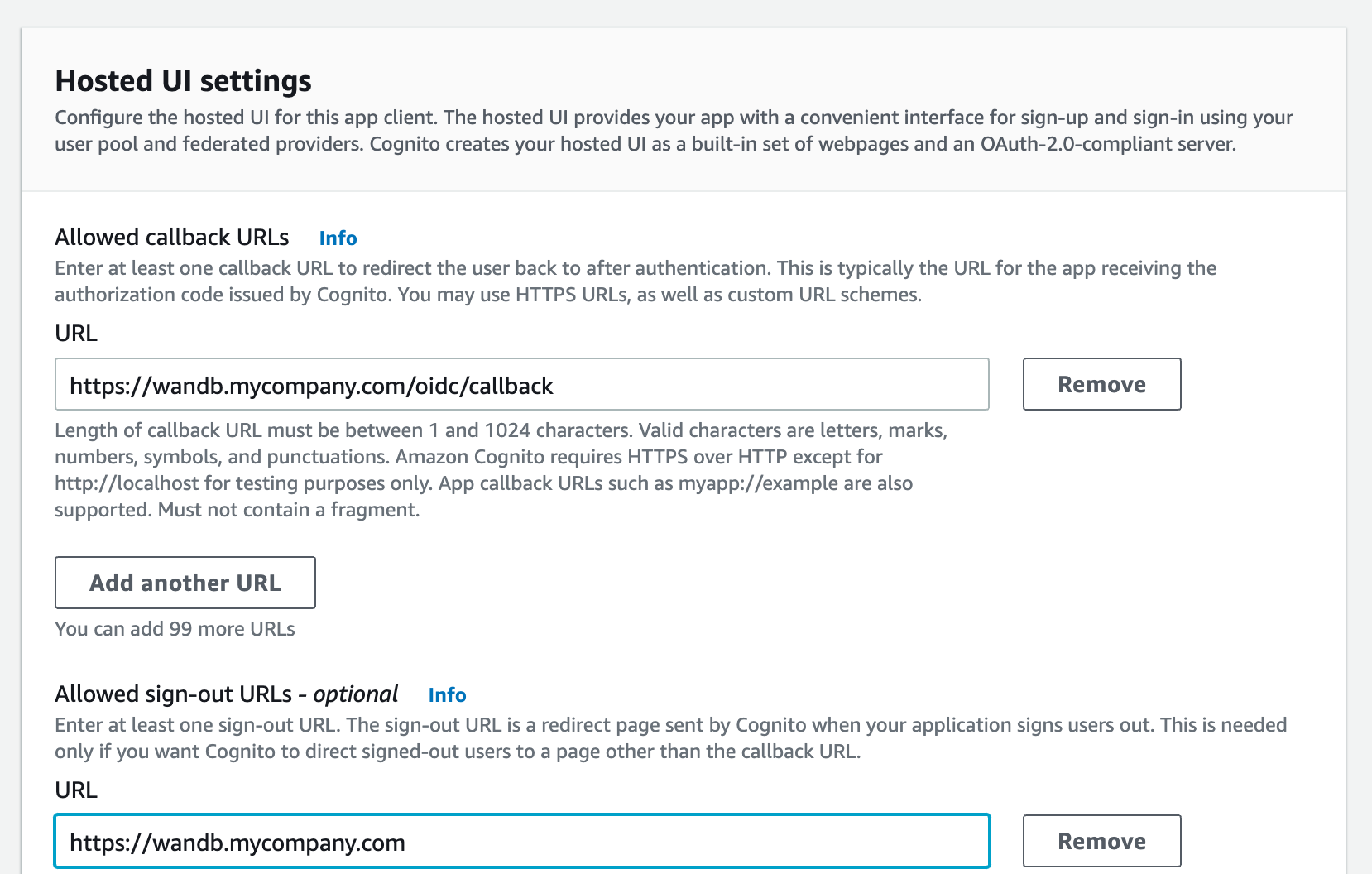
Provide an allowed callback URL to configure the application in your IdP:
- Add
http(s)://YOUR-W&B-HOST/oidc/callbackas the callback URL. ReplaceYOUR-W&B-HOSTwith your W&B host path.
- Add
-
If your IdP supports universal logout, set the Logout URL to
http(s)://YOUR-W&B-HOST. ReplaceYOUR-W&B-HOSTwith your W&B host path.For example, if your application was running at
https://wandb.mycompany.com, you would replaceYOUR-W&B-HOSTwithwandb.mycompany.com.The image below demonstrates how to provide allowed callback and sign-out URLs in AWS Cognito.
wandb/local uses the
implicitgrant with theform_postresponse type by default.You can also configure wandb/local to perform an
authorization_codegrant that uses the PKCE Code Exchange flow. -
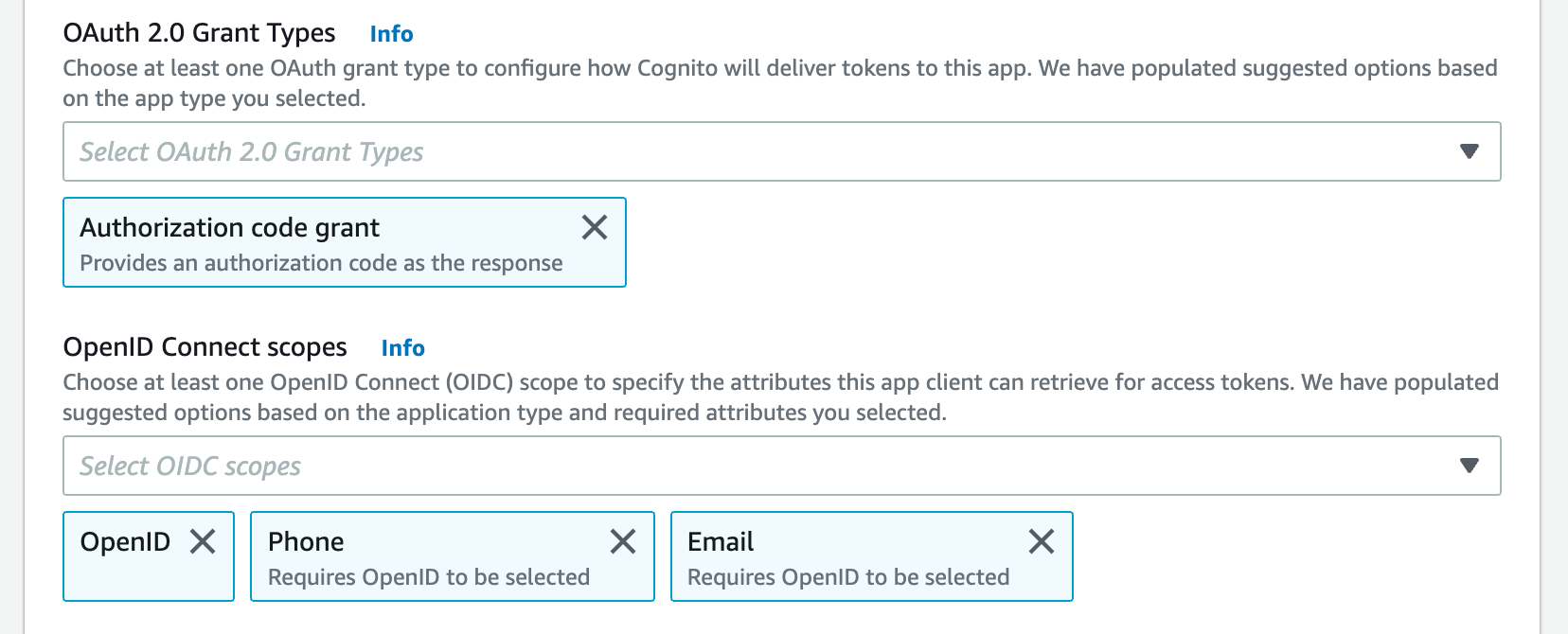
Select one or more OAuth grant types to configure how AWS Cognito delivers tokens to your app.
-
W&B requires specific OpenID Connect (OIDC) scopes. Select the following from AWS Cognito App:
- “openid”
- “profile”
- “email”
For example, your AWS Cognito App UI should look similar to the following image:
Select the Auth Method in the settings page or set the OIDC_AUTH_METHOD environment variable to tell wandb/local which grant to.
You must set the Auth Method to
pkce. -
You need a Client ID and the URL of your OIDC issuer. The OpenID discovery document must be available at
$OIDC_ISSUER/.well-known/openid-configurationFor example, , you can generate your issuer URL by appending your User Pool ID to the Cognito IdP URL from the App Integration tab within the User Pools section:
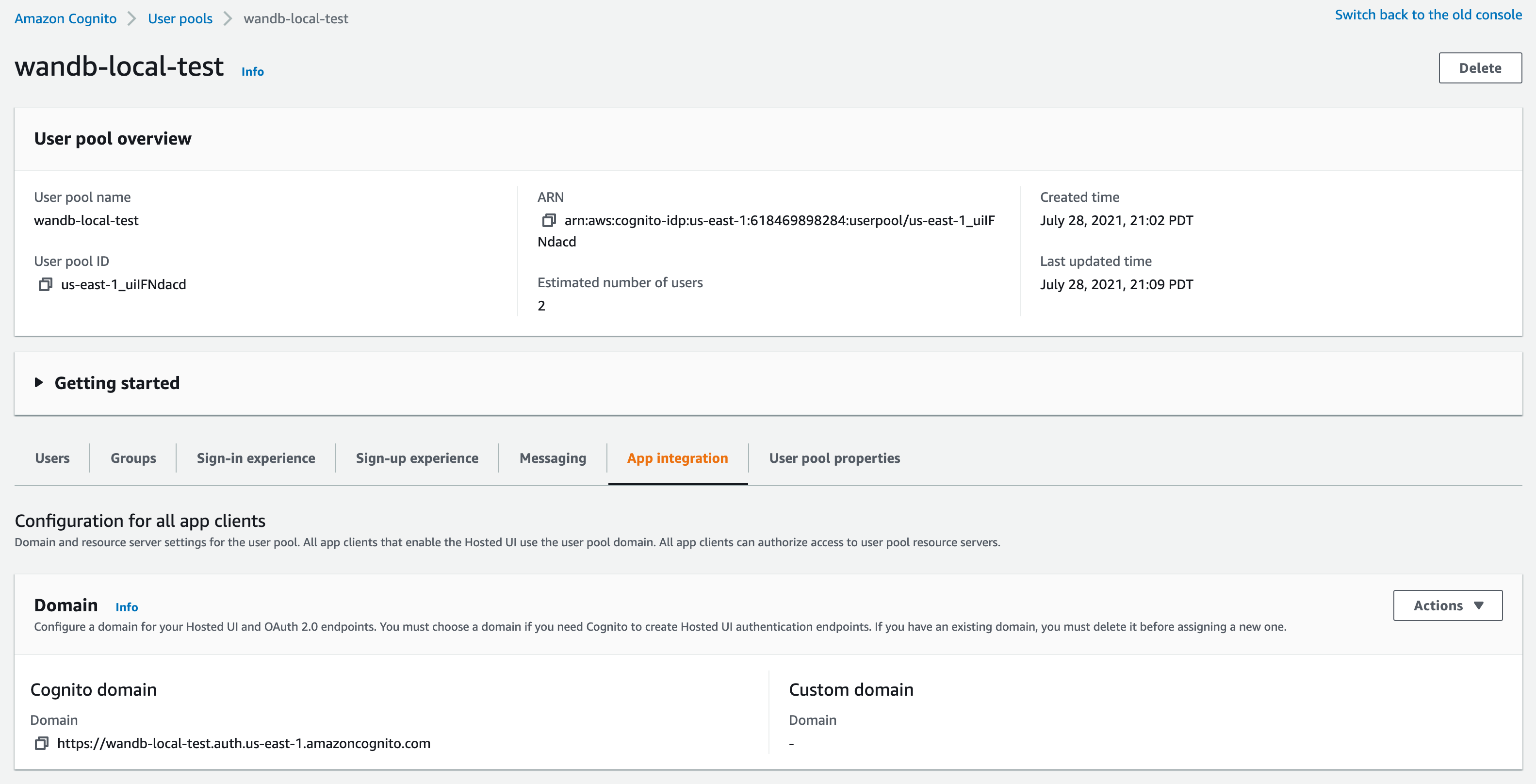
Do not use the “Cognito domain” for the IDP URL. Cognito provides it’s discovery document at
https://cognito-idp.$REGION.amazonaws.com/$USER_POOL_ID
Follow the procedure below to set up Okta for authorization:
-
Login to the Okta Portal at https://login.okta.com/.
-
On the left side, select Applications and then Applications again.
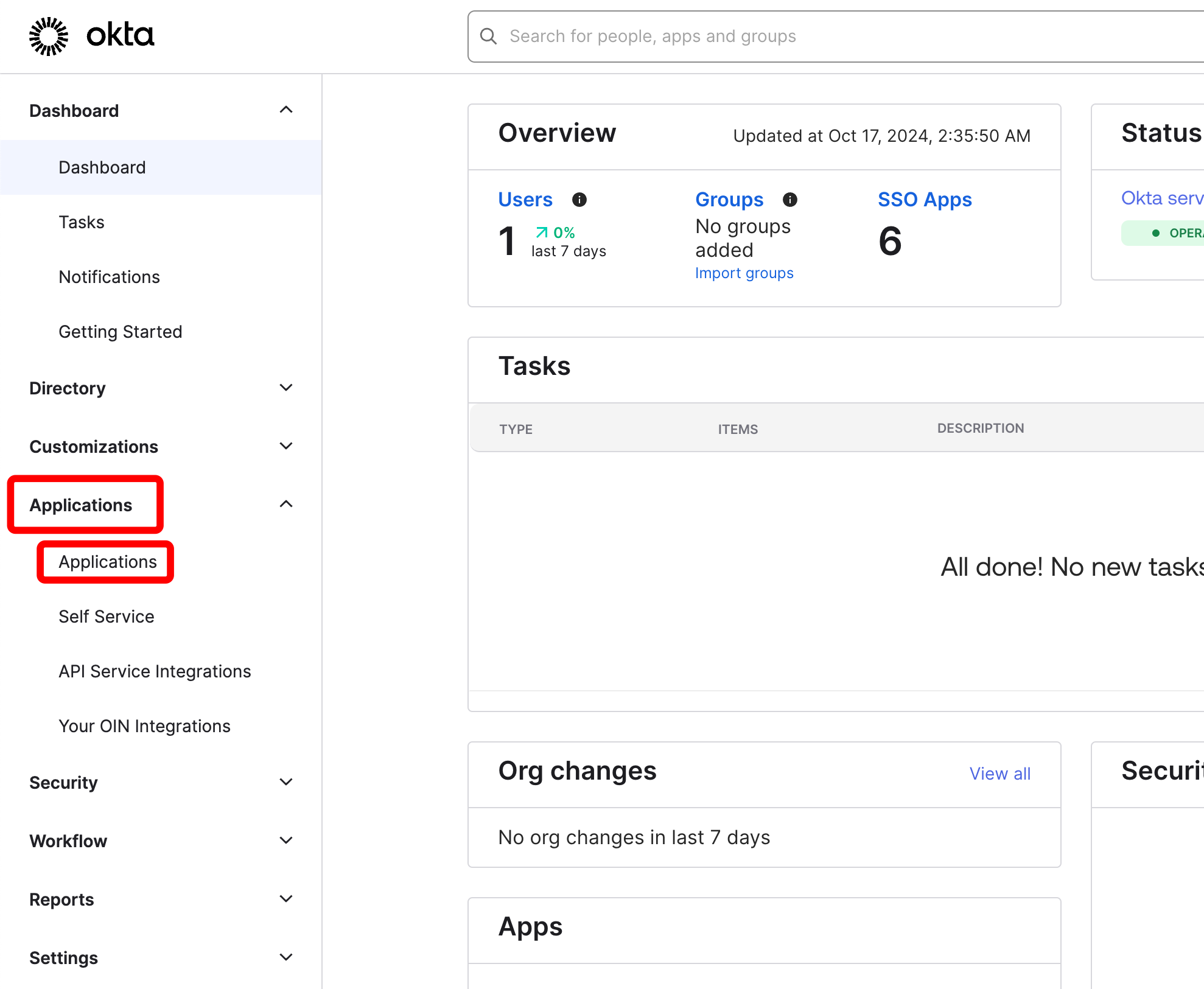
-
Click on “Create App integration.”
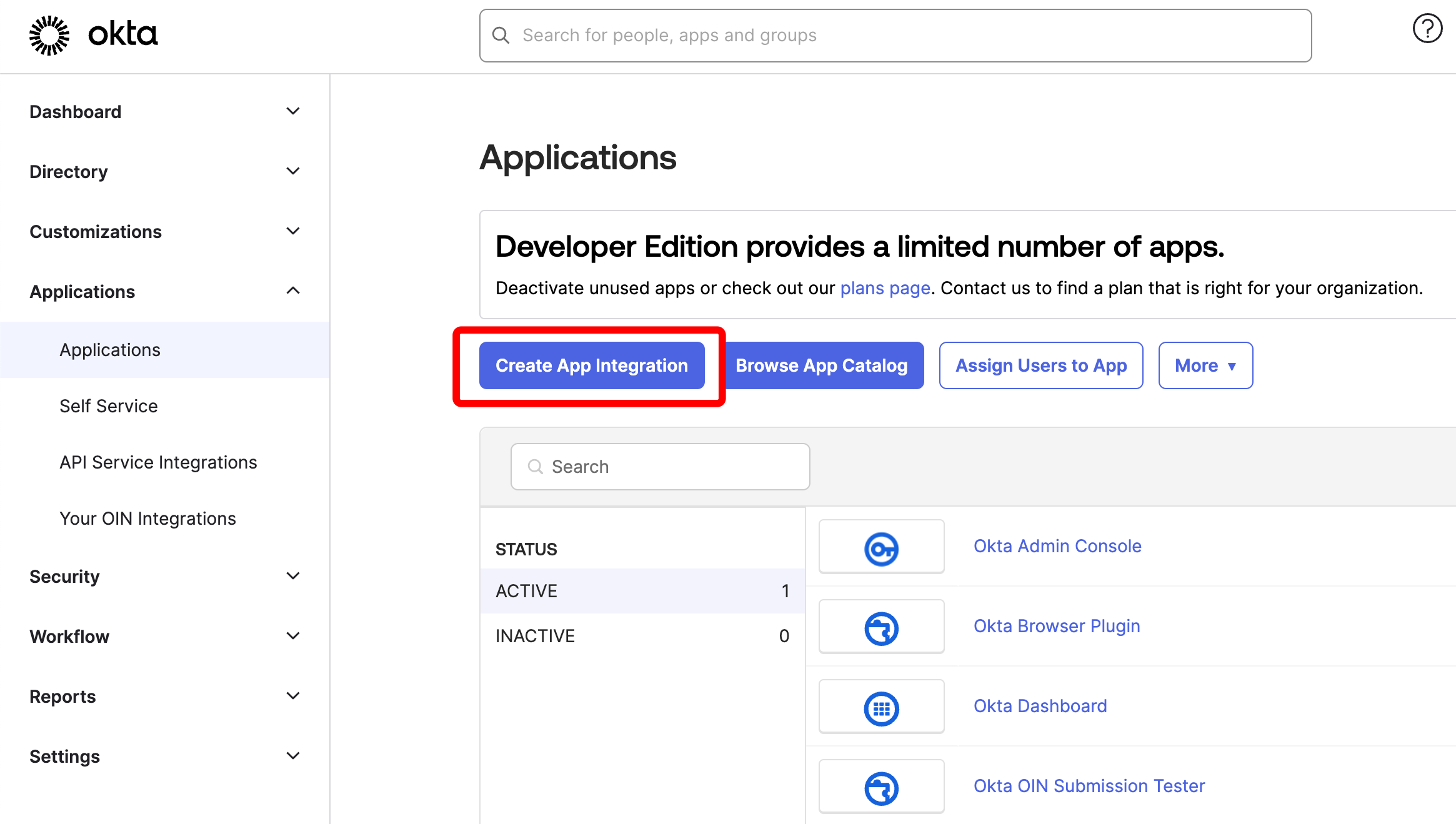
-
On the screen named “Create a new app integration,” select OIDC - OpenID Connect and Single-Page Application. Then click “Next.”
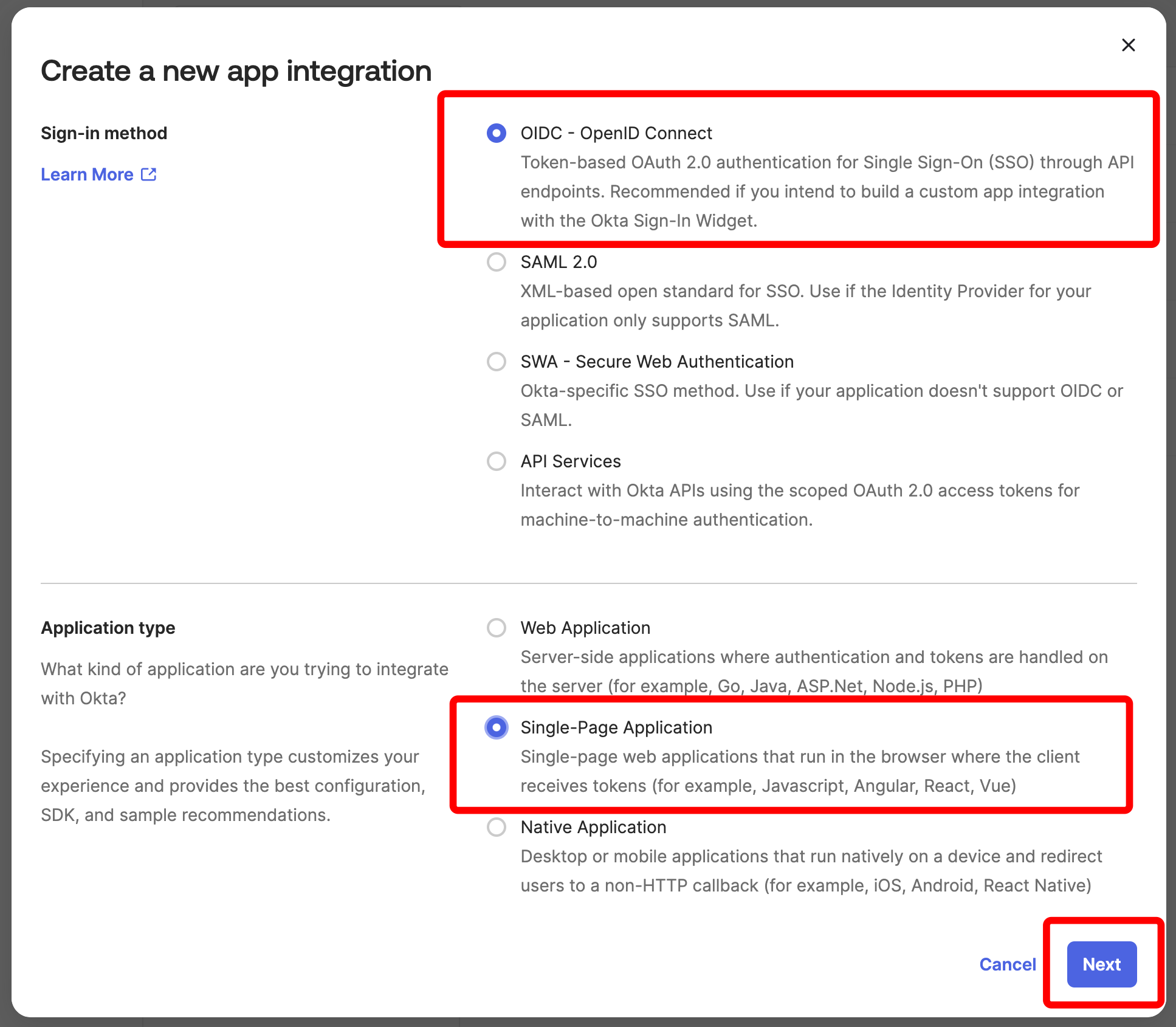
-
On the screen named “New Single-Page App Integration,” fill out the values as follows and click Save:
- App integration name, for example “Weights & Biases”
- Grant type: Select both Authorization Code and Implicit (hybrid)
- Sign-in redirect URIs: https://YOUR_W_AND_B_URL/oidc/callback
- Sign-out redirect URIs: https://YOUR_W_AND_B_URL/logout
- Assignments: Select Skip group assignment for now
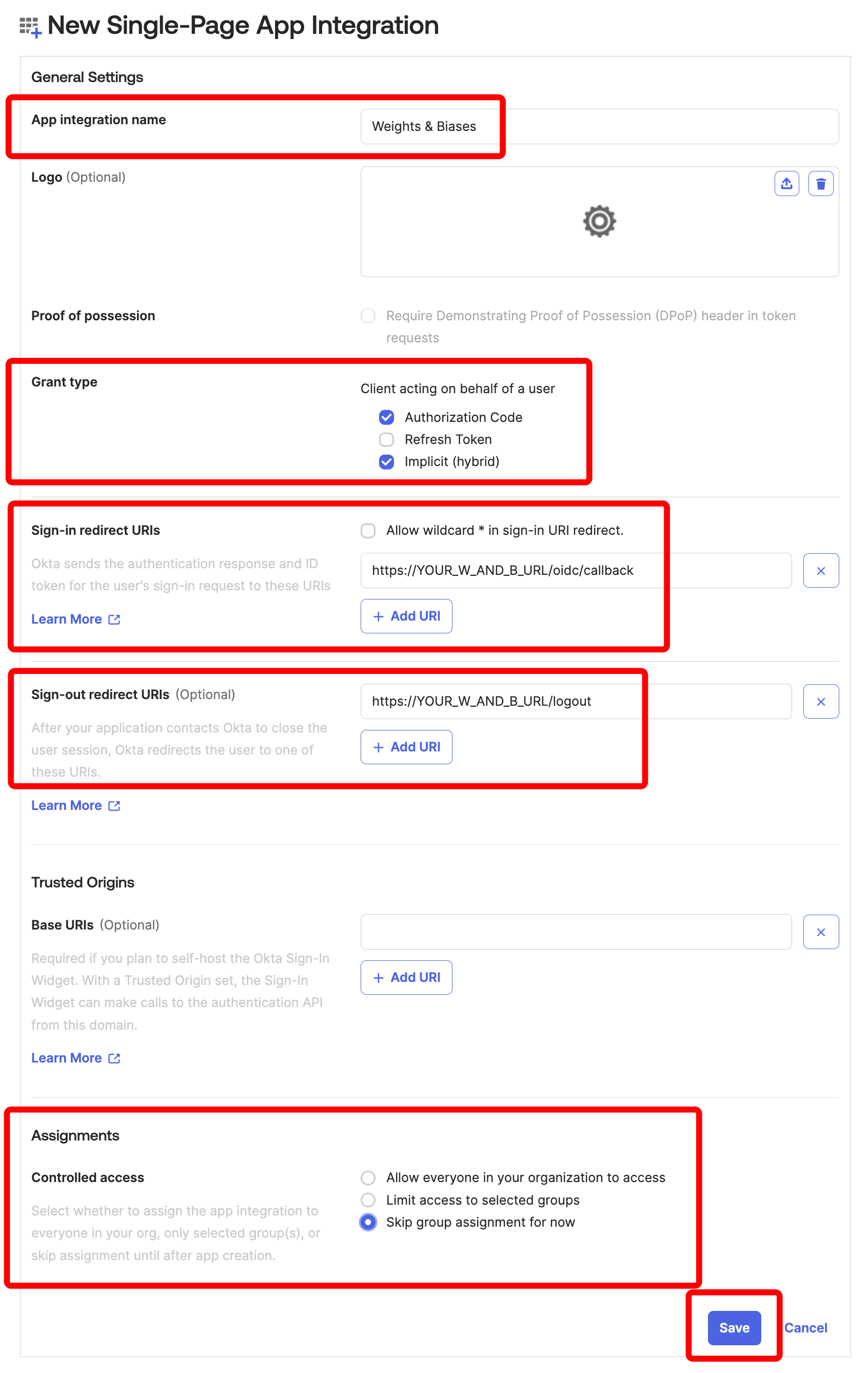
-
On the overview screen of the Okta application that you just created, make note of the Client ID under Client Credentials under the General tab:
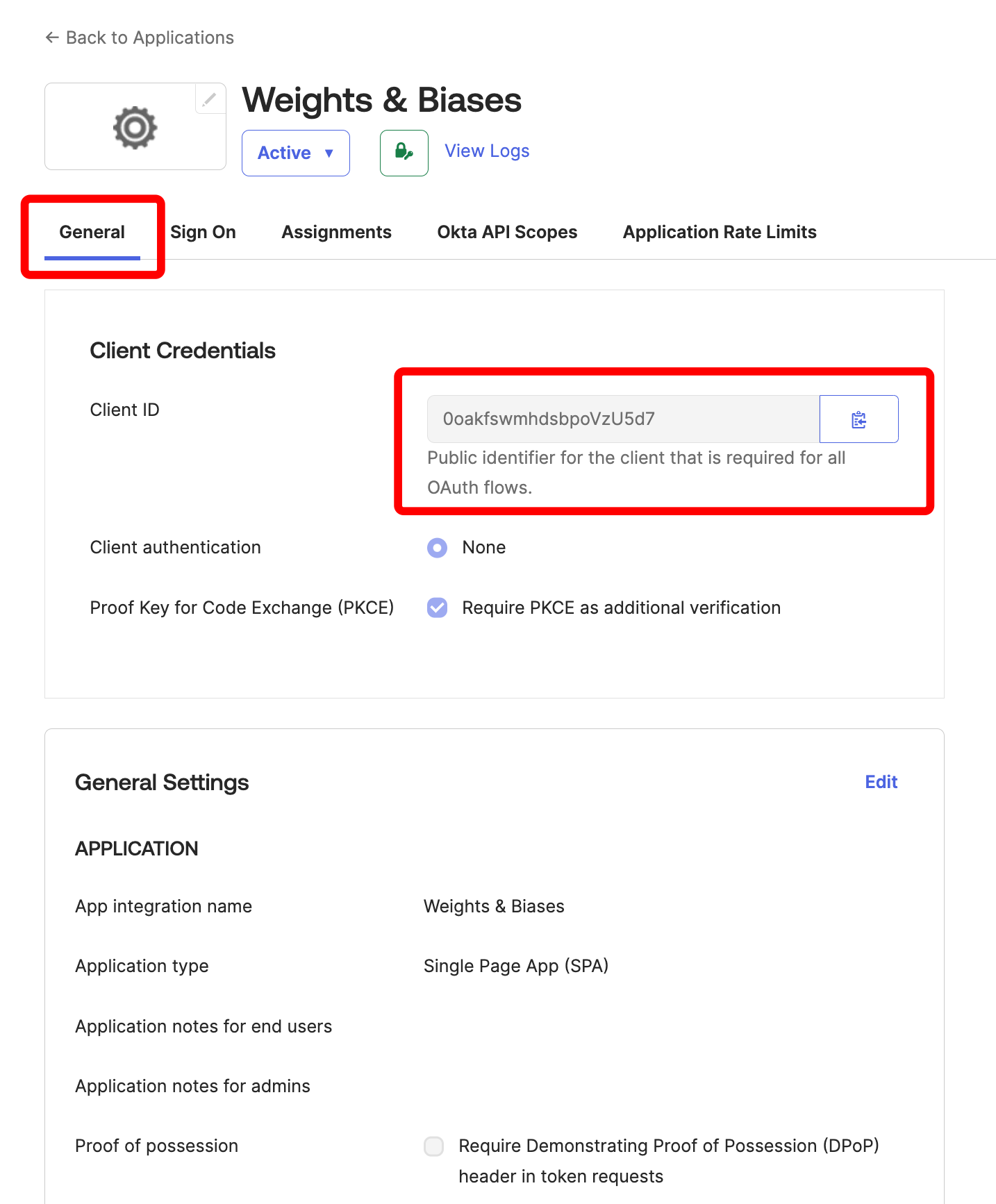
-
To identify the Okta OIDC Issuer URL, select Settings and then Account on the left side. The Okta UI shows the company name under Organization Contact.
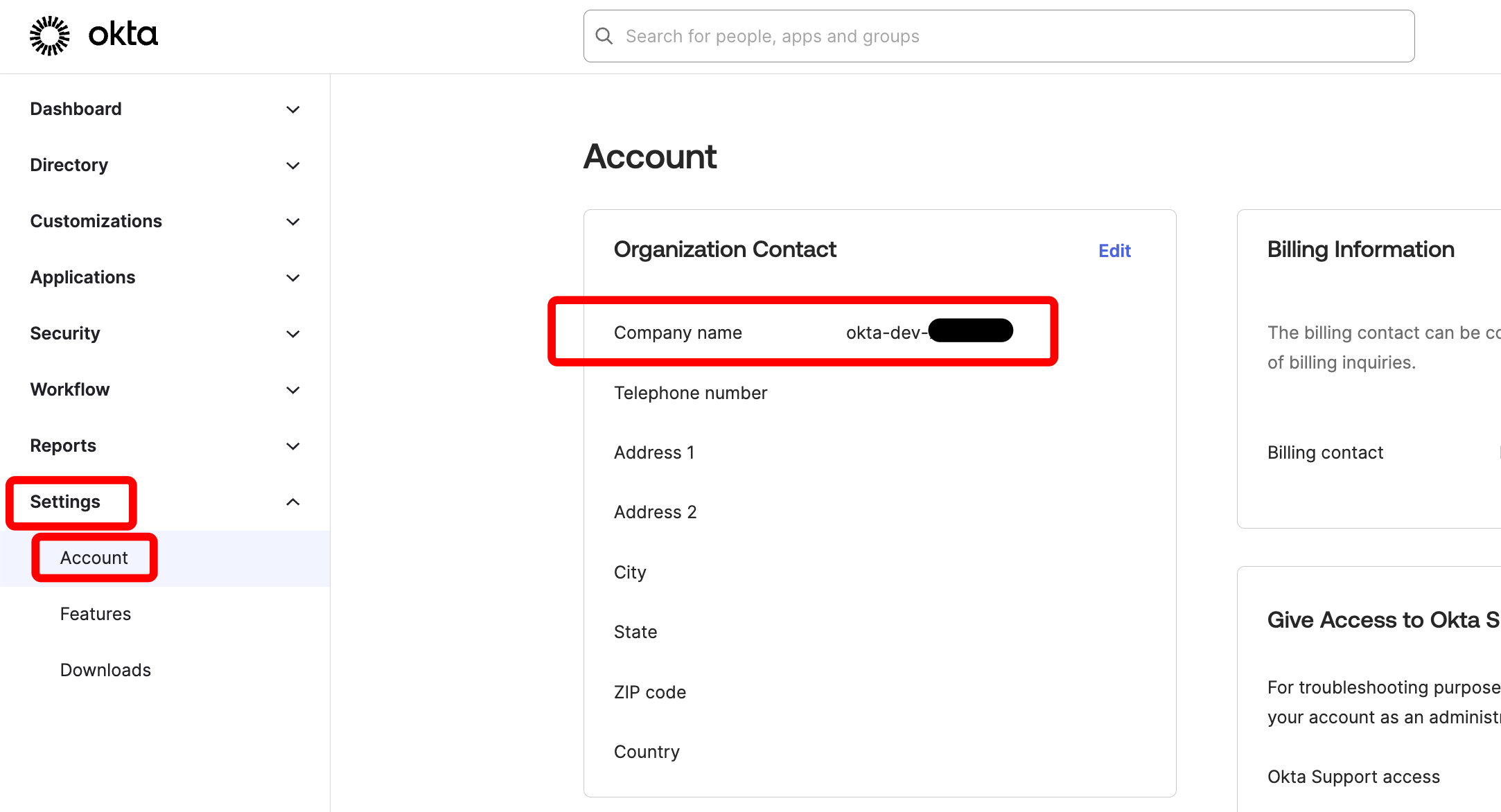
The OIDC issuer URL has the following format: https://COMPANY.okta.com. Replace COMPANY with the corresponding value. Make note of it.
-
Login to the Azure Portal at https://portal.azure.com/.
-
Select “Microsoft Entra ID” service.
-
On the left side, select “App registrations.”
-
On the top, click “New registration.”
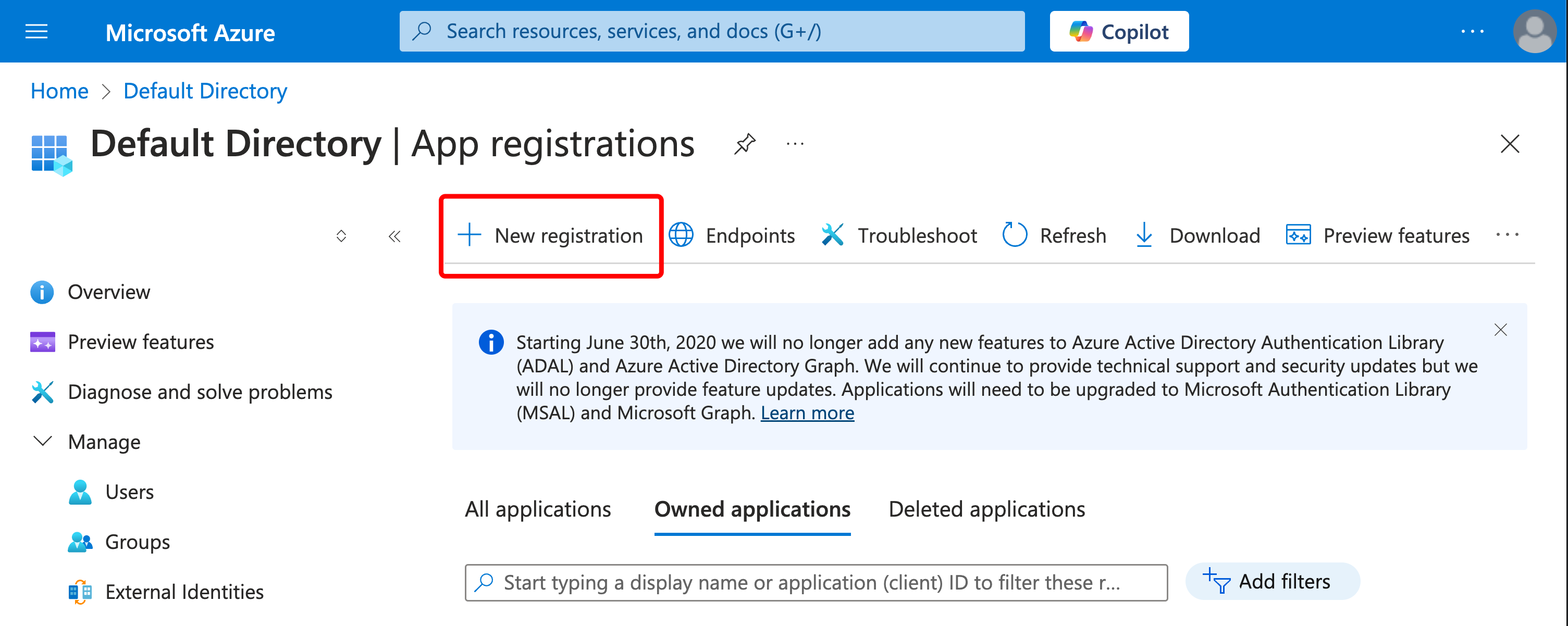
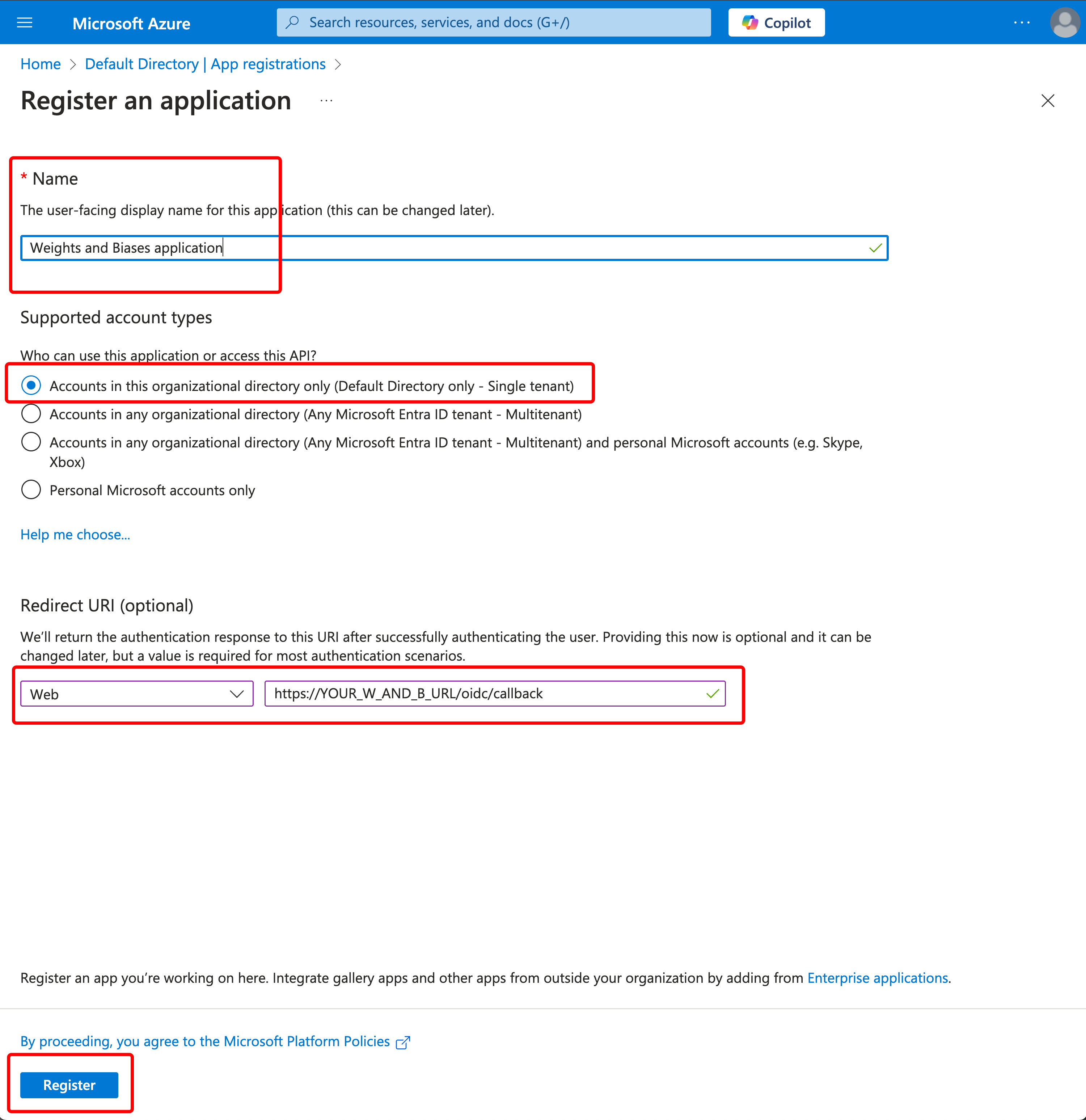
On the screen named “Register an application,” fill out the values as follows:
-
Specify a name, for example “Weights and Biases application”
-
By default the selected account type is: “Accounts in this organizational directory only (Default Directory only - Single tenant).” Modify if you need to.
-
Configure Redirect URI as type Web with value:
https://YOUR_W_AND_B_URL/oidc/callback -
Click “Register.”
-
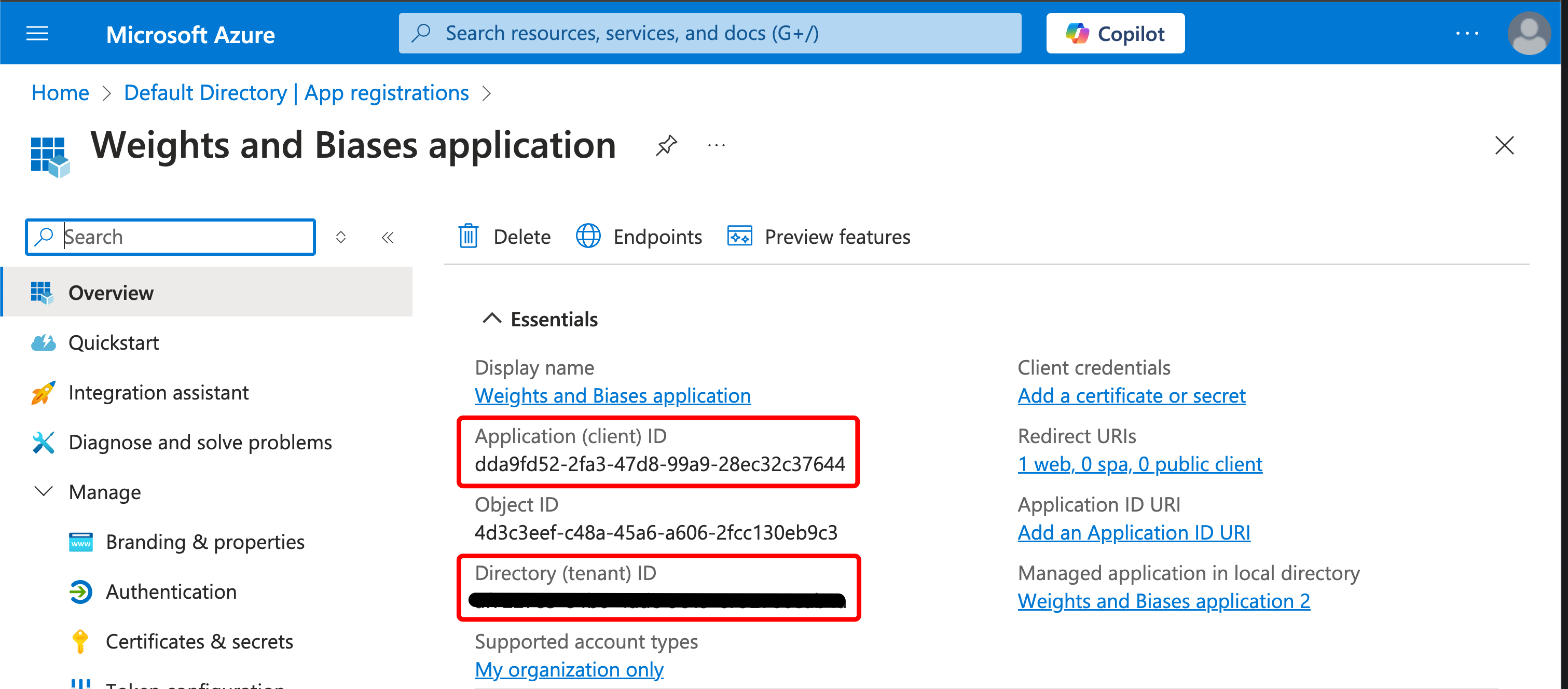
Make a note of the “Application (client) ID” and “Directory (tenant) ID.”
-
-
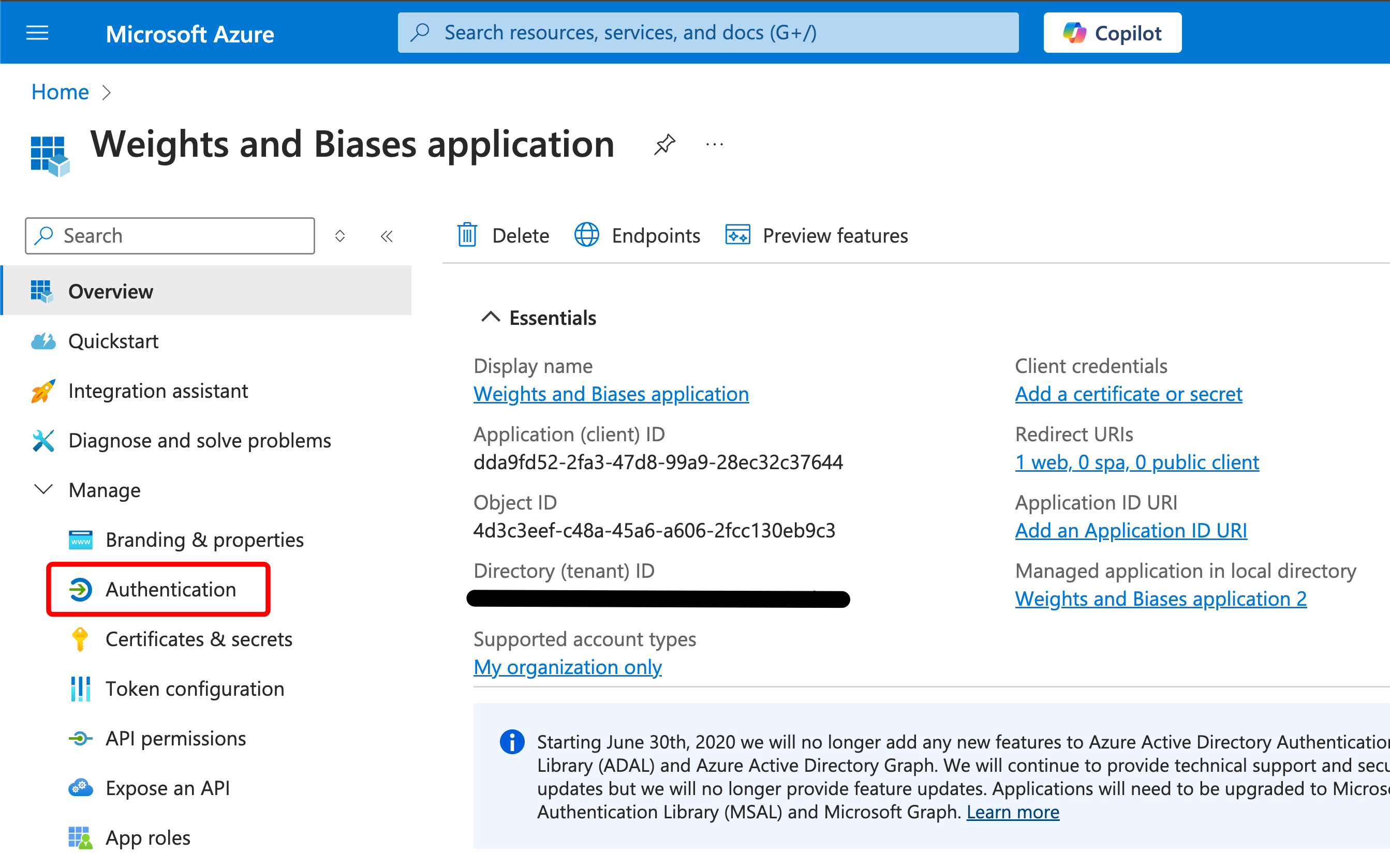
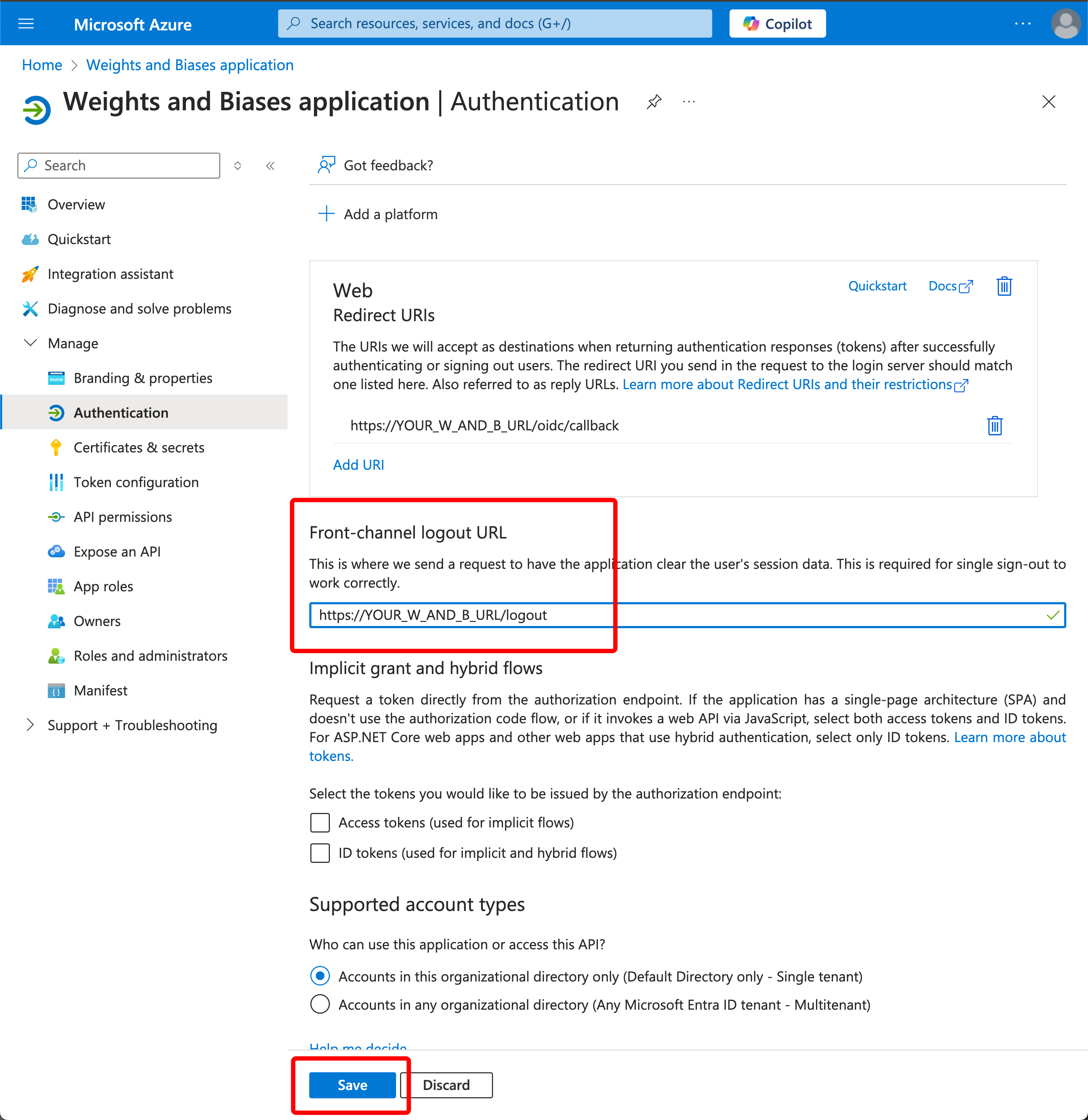
On the left side, click Authentication.
-
Under Front-channel logout URL, specify:
https://YOUR_W_AND_B_URL/logout -
Click “Save.”
-
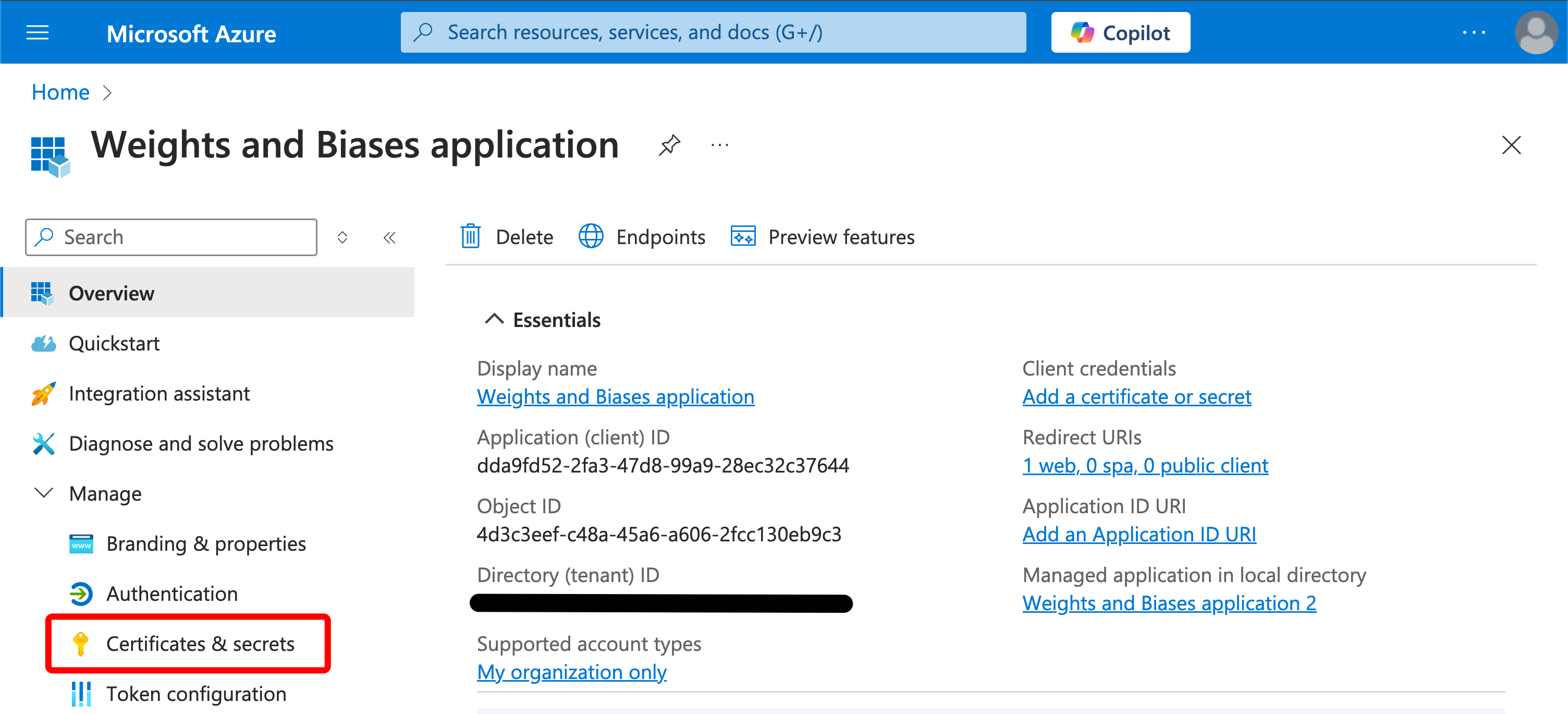
-
On the left side, click “Certificates & secrets.”
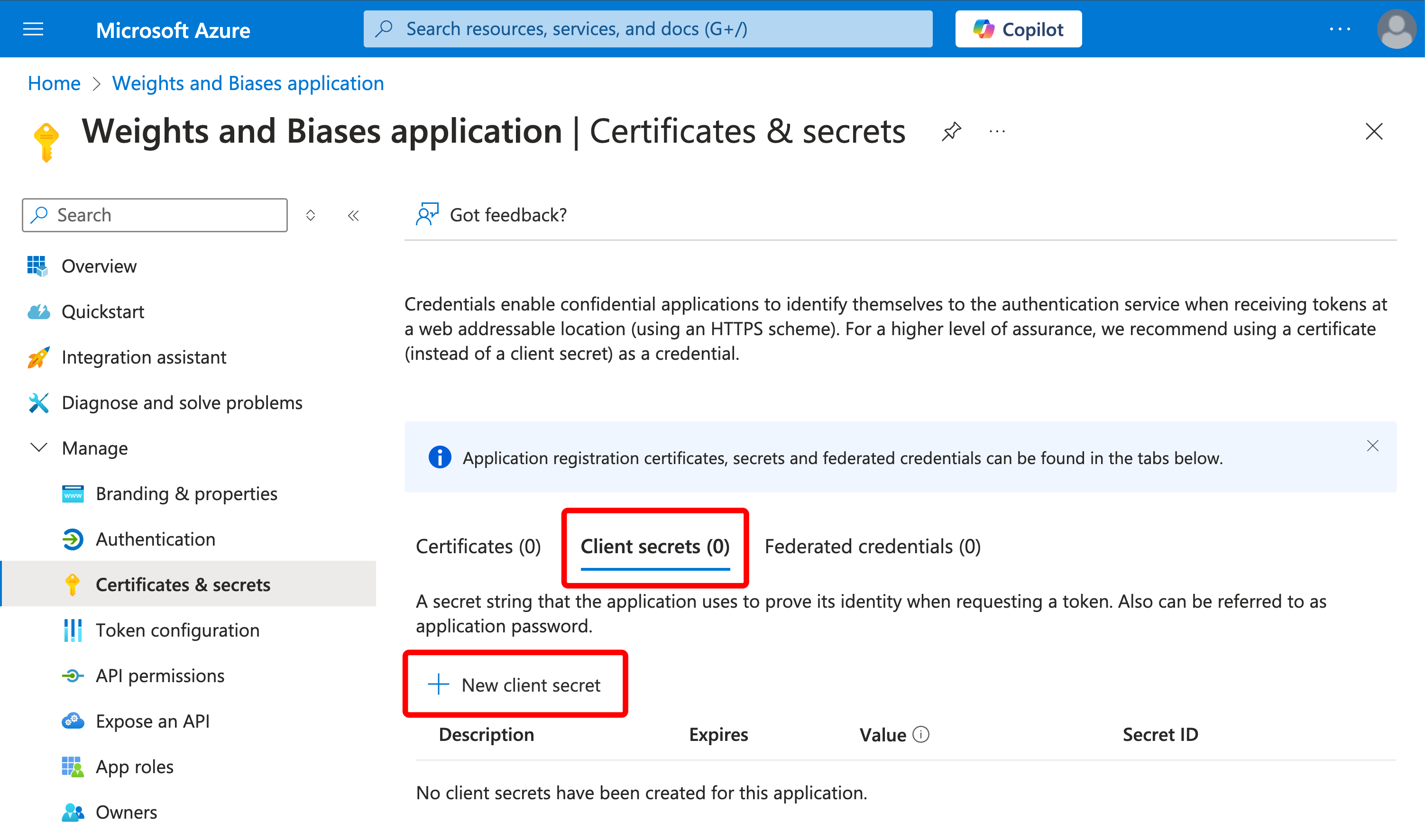
-
Click “Client secrets” and then click “New client secret.”
On the screen named “Add a client secret,” fill out the values as follows:
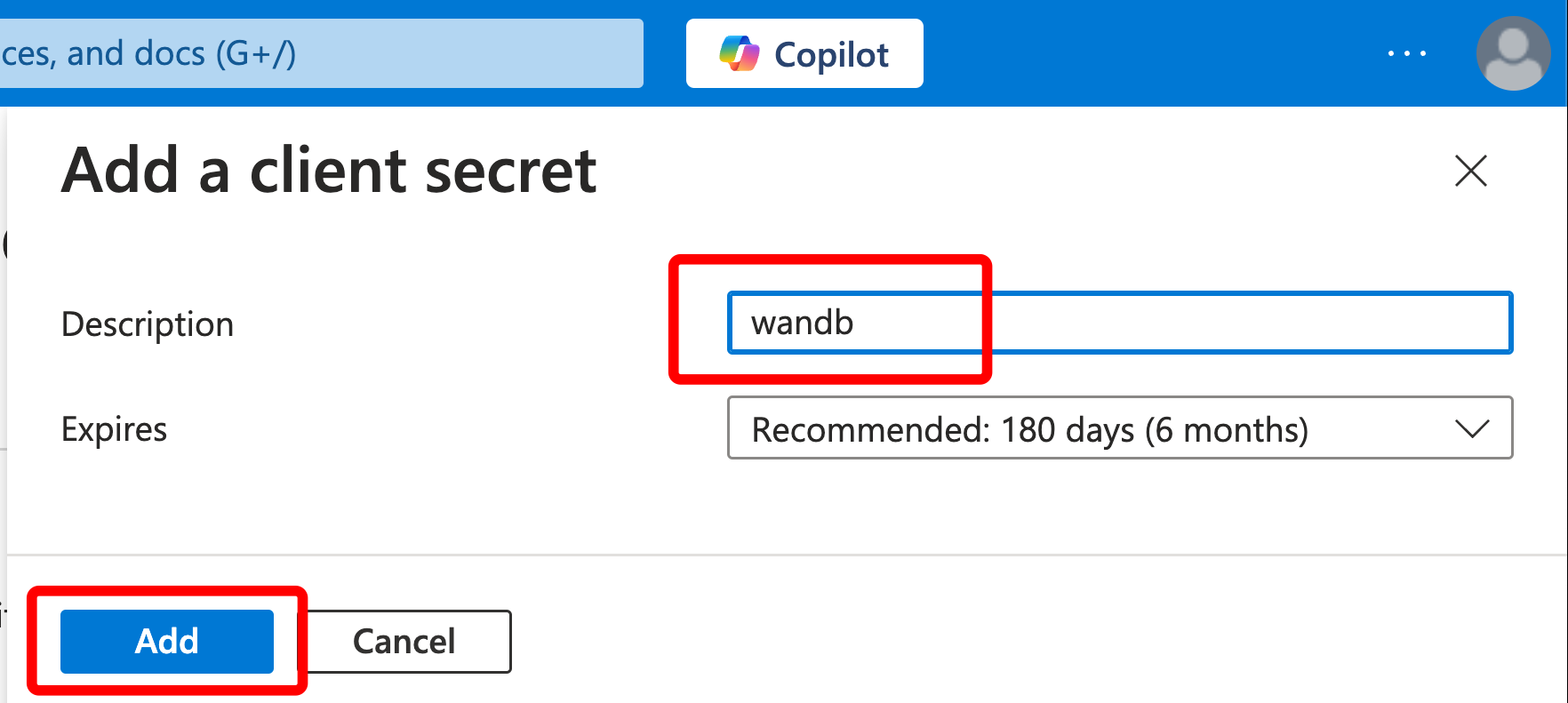
- Enter a description, for example “wandb”
- Leave “Expires” as is or change if you have to.
- Click “Add.”
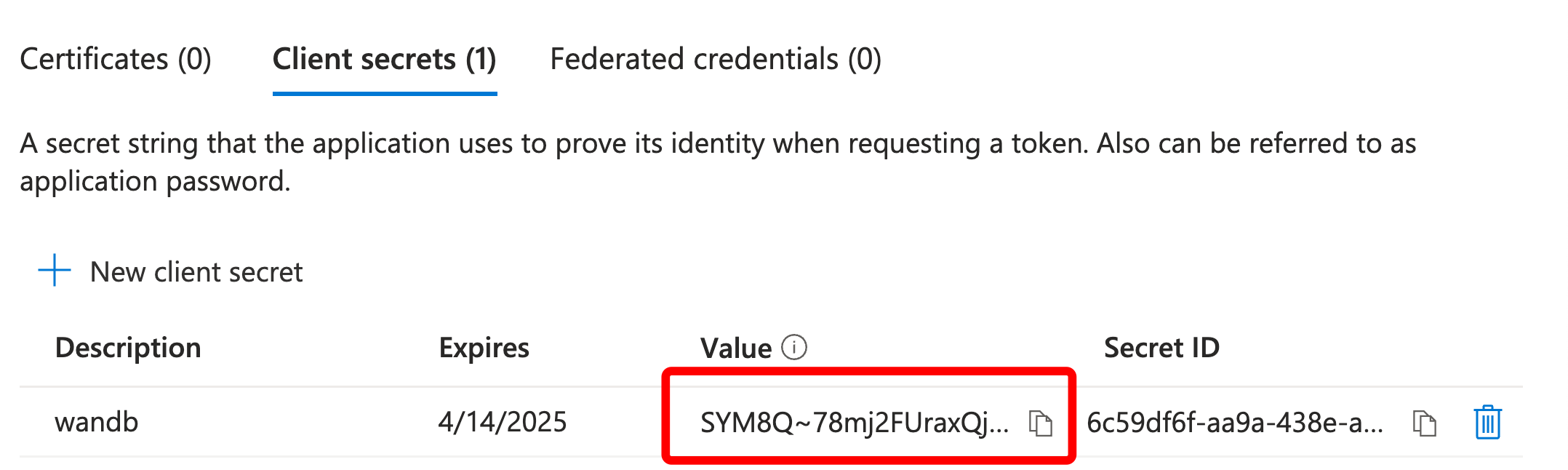
-
Make a note of the “Value” of the secret. There is no need for the “Secret ID.”
-
You should now have made notes of three values:
- OIDC Client ID
- OIDC Client Secret
- Tenant ID is needed for the OIDC Issuer URL
The OIDC issuer URL has the following format: https://login.microsoftonline.com/${TenantID}/v2.0
Set up SSO on the W&B Server
To set up SSO, you need administrator privileges and the following information:
- OIDC Client ID
- OIDC Auth method (
implicitorpkce) - OIDC Issuer URL
- OIDC Client Secret (optional; depends on how you have setup your IdP)
If your IdP requires a OIDC Client Secret, specify it by passing the environment variables OIDC_CLIENT_SECRET.
- In the UI, go to System Console > Settings > Advanced > User Spec and add
OIDC_CLIENT_SECRETto theextraENVsection as shown below. - In Helm, configure
values.global.extraEnvas shown below.
values:
global:
extraEnv:
OIDC_CLIENT_SECRET="<your_secret>"
LOCAL_RESTORE=true environment variable set. This outputs a temporary password to the containers logs and disables SSO. Once you’ve resolved any issues with SSO, you must remove that environment variable to enable SSO again.The System Console is the successor to the System Settings page. It is available with the W&B Kubernetes Operator based deployment.
-
Refer to Access the W&B Management Console.
-
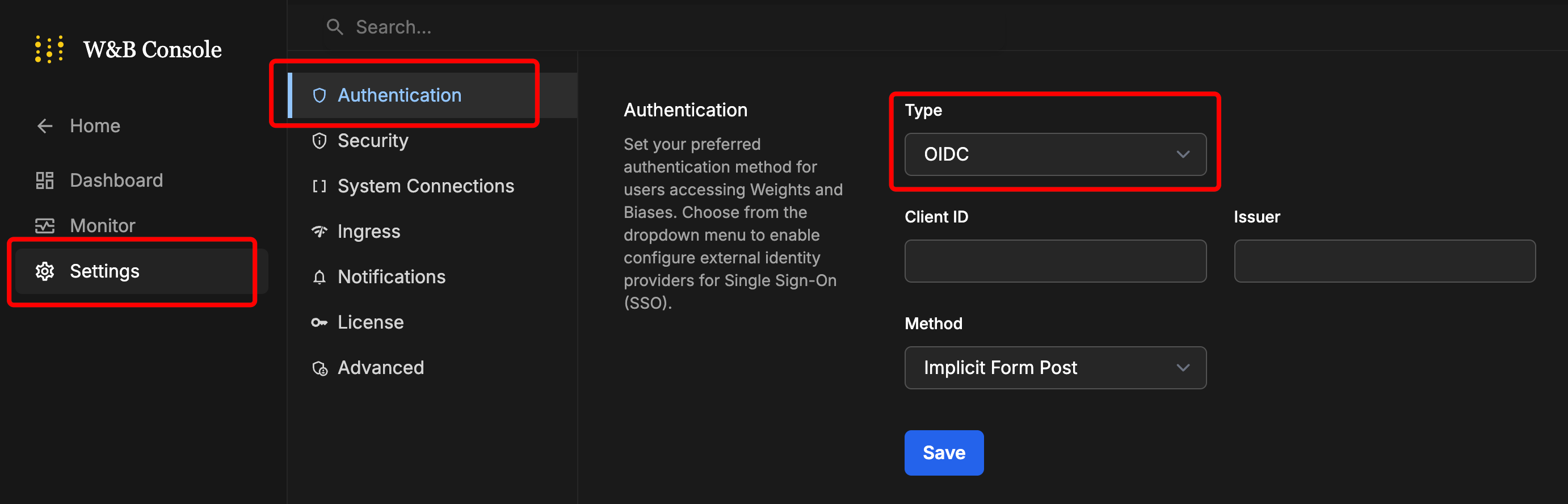
Navigate to Settings, then Authentication. Select OIDC in the Type dropdown.
-
Enter the values.
-
Click on Save.
-
Log out and then log back in, this time using the IdP login screen.
-
Sign in to your Weights&Biases instance.
-
Navigate to the W&B App.
-
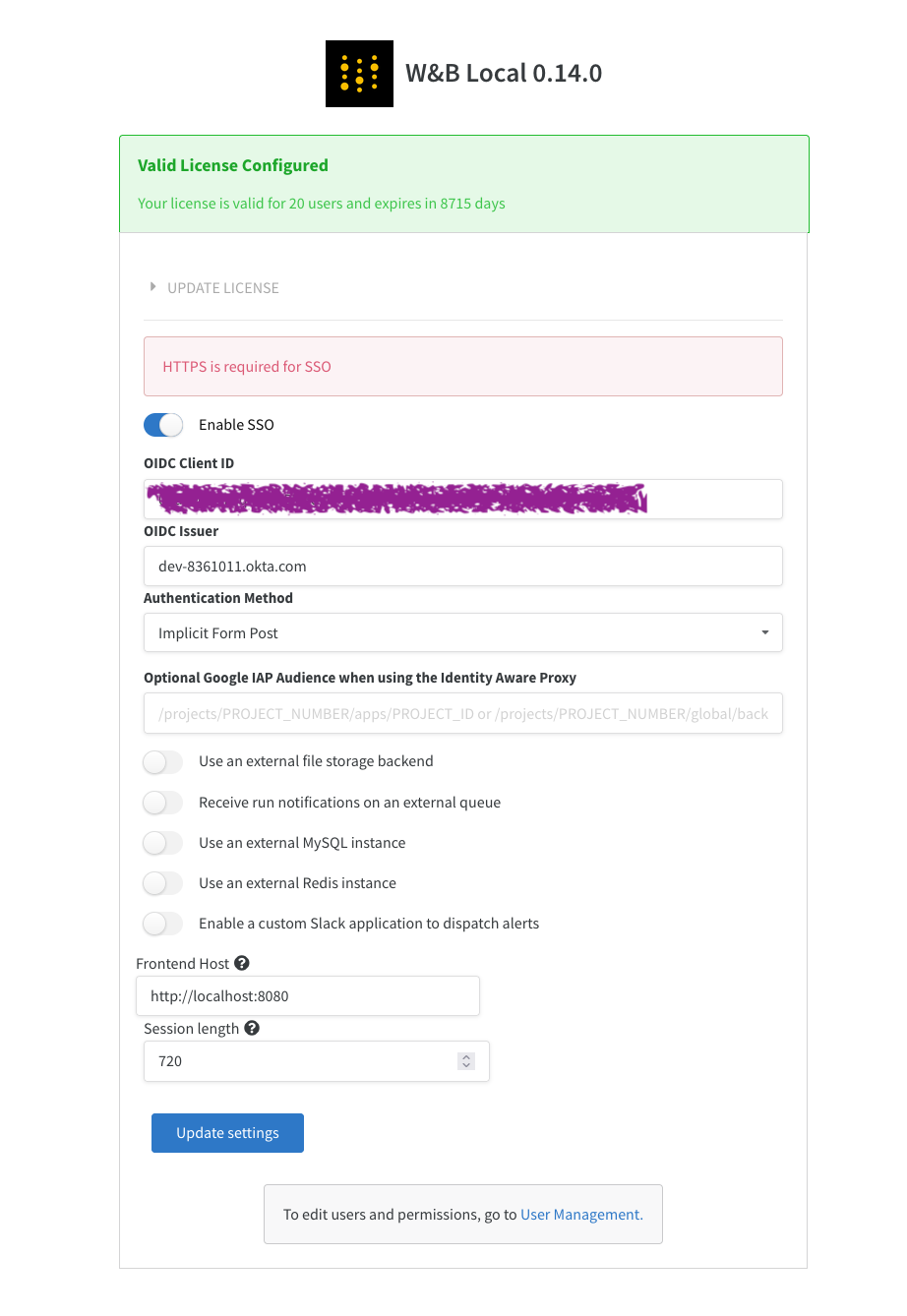
From the dropdown, select System Settings:
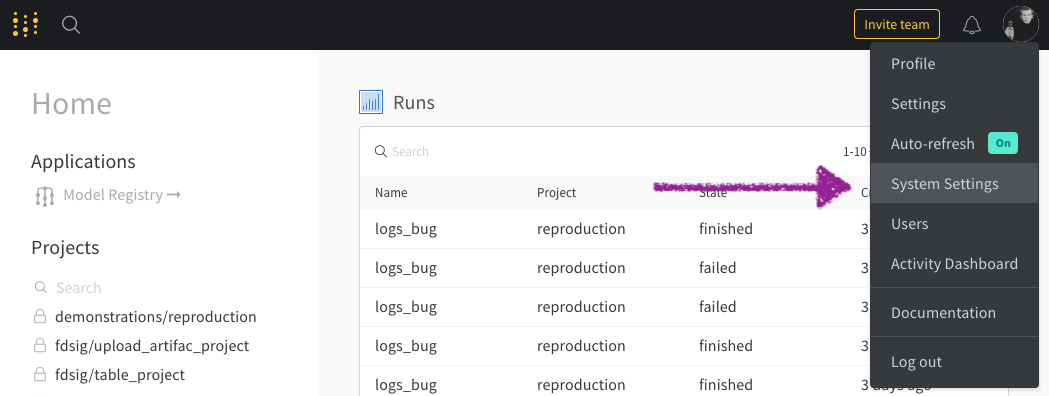
-
Enter your Issuer, Client ID, and Authentication Method.
-
Select Update settings.
LOCAL_RESTORE=true environment variable set. This outputs a temporary password to the containers logs and turn off SSO. Once you’ve resolved any issues with SSO, you must remove that environment variable to enable SSO again.Security Assertion Markup Language (SAML)
W&B Server does not support SAML.
Feedback
Was this page helpful?
Glad to hear it! If you have further feedback, please let us know.
Sorry to hear that. Please tell us how we can improve.